Today, the fight against crime and cybercrime has become increasingly complex and more and more data needs to be analysed and structured. To meet these challenges effectively, law enforcement agencies (LEA) need to build a powerful investigation management system based on policing processes (RMS) in order to facilitate cooperation between forces and improve inter-agency collaboration, enhance communication and evolving regulations.
What we offer
The Eviden Investigation Management solution is a fully end to end investigation platform, AI enabled analytics, geospatial mapping and visualization tools, it covers all functionality you need in your day-to-day police records management tasks.

Use cases
Global offering of policing use-cases

Fight against cybercrime
Our investigation management offering allows to couple investigation with forensic digital tools to detect, prevent, and prosecute illegal online activities such as hacking, identity theft, and fraud. It allows to involve in the same solution multiple Police & Justice departments around the world in order to collaborate and resolve cases.

Lawful interception
Collaboration between LEAs and the judiciary is key for full compliance with privacy legislation. Our solution allows LEAs to monitor and collect investigation data authorized by judicial warrants efficiently. How? By linking our investigation management system with lawful interception centers, all strictly within legal boundaries.

Financial crime
Analyzing financial documents and transactions for financial crime as fraud, money laundering, terrorist financing, bribery & corruption, insider trading evidence are quite complex and may be long lasting in time. Our investigation solution allows to analyze financial related data & big data but also couples it to third party solution multi-int solutions as OSINT.

Money laundering
Criminality moves illegally funds around the globe using different channels as banks, shell companies, intermediaries and money transmitters, attempting to integrate the illegal funds in legal corporations and society economies. Our solution allows to collect and analyze any information, financial but not only that might help identify suspicious patterns and potential sources of illicit funds: financial transactions, customer behavior, and other relevant data.

Day-to-day crime
Our investigation solution connects and analyses diverse data points to illustrate relationships between entities as people, places, and assets, facilitating sophisticated criminal investigations. The solutions allows to manage cases, evidence and all related reports. Intelligence analysts and investigators can find online links that result in case closures and successful prosecutions by using our web investigation tools. Our system is also utilized to identify possible criminal behavior on the internet.

Cold Cases
Cold cases are criminal investigations that are open for a long time - years or even decades - before they are resolved; investigations that will manipulate a number of data during all these years. Solving a cold case can be an incredibly challenging and complex process. Our investigation solution allows to structure investigation data throughout the time in order to help investigator move forward and solve cases.
A centralized hub for your investigations
Fully configurable platform gathering critical investigative data including evidence and documents. This centralized hub facilitates information and intelligence sharing both within and beyond the organization.
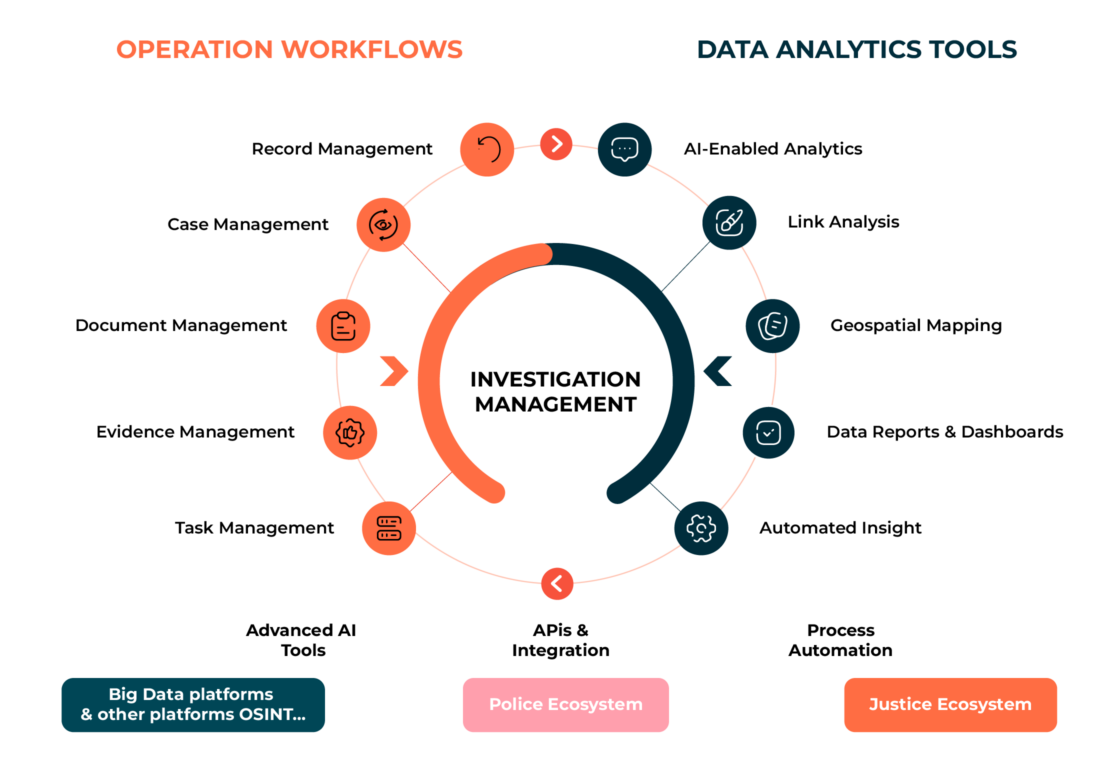
Key benefits
• Easy-to-use specialized software solution • Save time entering data • Access and feed the system
• Share data with partner organizations • Communicate via chat features • Create and share notes • Use the mobile app
• Automate search process • Generate automated, compliant reports and dashboards
• Strengthen user authentication and access management • Encrypt data
• Operate various levels of information access to comply to right now
• Control the records to comply with regulations • Can be adapted to specific regulations
Contact us



