Google’s Trusted Cloud
Security is top of mind throughout all businesses and large organizations. In 2023, the global average cost of a data breach reached USD 4.45 million. Notably, 82% of these breaches involved data stored in the cloud.
It follows that organizations need solutions that offer comprehensive visibility across hybrid environments and safeguard data as it moves between clouds, databases, applications and services.
For those using Google Cloud, leveraging its cloud-native security features can help achieve these objectives. But where should you begin, and how can you accelerate secure cloud adoption?
In order to determine which cloud security solutions are most effective, it is critical to first evaluate the organization’s existing security posture. This initial step allows identification of potential weaknesses and areas of improvement.
This initial focus is on understanding the division of security responsibilities of the cloud provider versus those of its customer. This is referred to as the shared responsibility model. According to this model, security responsibilities are divided between the cloud service provider and its customer. The specific elements that need protection vary by cloud model. However, ultimately, it is always the customer’s responsibility to secure its data in the cloud.
From shared responsibility to shared fate
With the shared-fate model for a trusted cloud, Google emphasizes being an active cloud service partner for customers to deploy workloads securely instead of only determining where its own responsibility would end.
Through the shared-fate model, Google operates a layered security model to support customers by protecting workloads, users and assets using GCP security and resilience solutions to adopt the cloud securely. For this reason, Google has released the Security and Resilience Framework (SRF) to support the secure cloud adoption journey of its customers.
An overview of the SRF
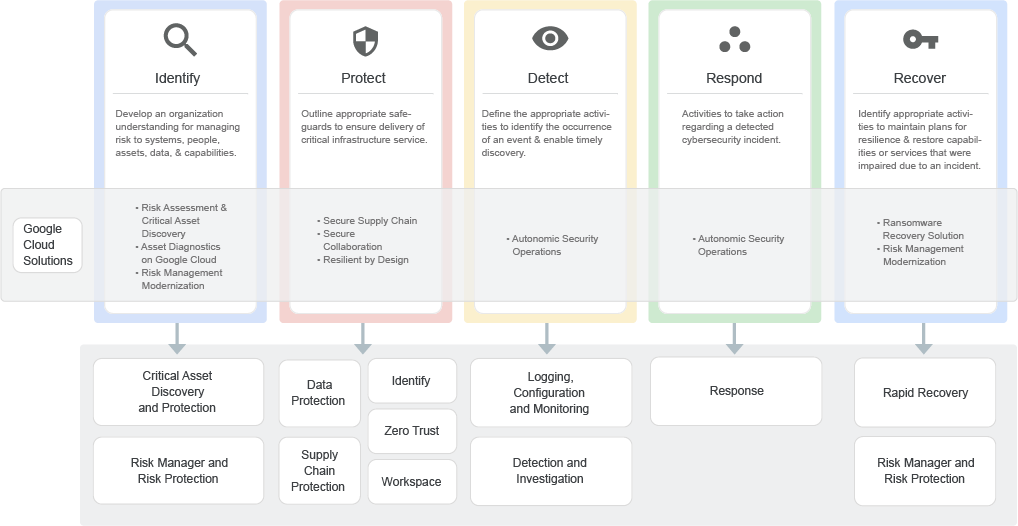
Google’s SRF is a programmatic, risk-based approach for secure cloud adoption. It aligns with industry security standards and best practices to strategically manage an organization’s security transformation program. The SRF is a foundational risk framework for secure adoption of Google Cloud by establishing a set of baseline security controls and mapping these to Google security solutions. The SRF also provides additional security controls for workloads running on GCP. These extra controls offer detection, response, and recovery capabilities to ensure the resilience of cloud workloads.
SRF’s 5 guiding principles
The SRF follows a risk-based approach based on the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). It defines guiding principles aligned with NIST to address each phase of the secure systems lifecycle. Guiding principles map to Google Cloud-native security solutions and corresponding asset types. Asset types are the assets that an organization needs to protect, encompassing users, data, applications, devices and networks.
The five principles are as follows:
- Identify: This provides an approach to managing security risk to cloud systems, people, assets, data and related capabilities. To achieve this, Google provides solutions for risk assessments through Google’s Risk Protection Program. There is also an offering for critical asset discovery through the Cloud Asset Inventory service. Google Cloud security services like Google Security Command Center can help to achieve asset inventory management and risk protection.
- Protect: This principle guides an organization to define safeguards for more secure and resilient critical infrastructure services. Google offers a solution to implement the zero trust model with BeyondCorp Enterprise via solutions such as the identity-aware proxy (IAP) to enable a flexible workforce without the need for VPN technologies. Google also protects against application security threats via Web App and API protection, including hybrid and multicloud scenarios. The protection principle also provides capabilities to mitigate the risk of supply chain threats via solutions such as Binary Authorization, allowing only trusted and verified workloads.
- Detect: This supports an organization in defining a set of activities to identify security-relevant events and enable timely investigation. Google drives SOC modernization via Autonomic Security Operations (ASO), combining a set of practices, tools and principled approaches.
With ASO, an organization can withstand attacks through an adaptive and automated method to threat management. A prime capability of the ASO suite is Google Security Operations and BigQuery, which allows scalable and modern threat detection particularly well suited for detecting security incidents in GCP workloads. - Respond: This establishes activities for actions required or the corresponding reaction when a security incident is detected. Incident response capabilities are enhanced through the Google Security Operations Suite, incorporating security orchestration and response (SOAR) via Chronicle. This solution also provides playbook automation, case management and integrated threat intelligence from Mandiant.
- Recover: In this principle, an organization identifies activities to allow the continuation of business operations in case of a breach. Google’s capabilities ensure business continuation against threats like ransomware through Google Cloud Backup and Disaster Recovery. This solution is a backup and disaster recovery vault with rapid access to a point-in-time copy of data, enabling a fast business recovery to an operational state from ransomware attacks.
For customers to get started with assessing and implementing these principles as part of their secure cloud adoption journey, Google provides the SRF checklist and the SRF discovery tool. These two mechanisms allow an organization to assess the cloud security posture and identify relevant control gaps.
Source:Google Cloud security and resilience framework
The SRF checklist and discovery
The SRF checklist is handy for an initial assessment and is available for Google customers to use. It gives an overview of Google’s cloud-native security capabilities mapped back to different guiding principles of SRF. It is particularly well suited for customers who are early in the cloud adoption journey.
This checklist provides a set of controls across different domains such as governance, risk management and threat management. The set of controls is aligned with Google’s security solution and helps to get a quick understanding of the overall cloud security maturity.
Next, is the SRF Discovery — a free questionnaire available on the Google Solutions Center. This questionnaire addresses customer concerns around security challenges and threats. It also provides objectives for security and compliance requirements to drive secure cloud adoption. With the SRF discovery tool, a customer can identify relevant control gaps within the SRF. Once completed, it helps a Google customer identify which solutions need to be implemented and provides a capability maturity score. The discovery also includes recommendations relating to the Google Cloud Architecture Framework and the Google Secure AI Framework (SAIF).
Together, the SRF checklist and its discovery tool guides organizations on how to optimize security capabilities for specific use cases, improving overall cloud security program maturity. Some use cases include web application and API protection, Google SecOps, and Zero Trust with BeyondCorp Enterprise.
The SRF scores the people, process and technology elements of cloud transformations and provides guidance for a customer to fully use Google Cloud Security capabilities for specific outcomes.
Benefits of SRF for secure cloud adoption
Accelerated secure cloud adoption: Google customers can benefit from SRF to align with best practices for securely migrating and operating workloads within GCP. The outcome of the SRF Google Cloud-native capabilities are aligned with each guiding principle, allowing customers to understand which Google security solutions to leverage.
Enhanced cloud security posture: With the help of the SRF guiding principles, customers can build a mature cloud security program, built upon GCP security best practices. The risk-based approach of SRF also provides customers with recommendations and a set of controls for Google Cloud security solutions to reduce the risk of security events resulting in data breaches and outages due to unauthorized access. If these controls are breached, the SRF provides response and recovery capabilities to ensure resilience. The SRF also helps in identifying threats against assets that the organization is aiming to protect (i.e. their “crown jewels”).
Recommendations for Google Cloud security solutions: The output of the SRF is a capability maturity assessment score with recommendations mapping back to Google Cloud security solutions. The output can be used as a road map for the secure cloud adoption journey and highlighting specific use cases for remediating security-gap control using Google solution guidance. The solution guidance allows reducing risk using Google Cloud security best practices.
Security and resilience as business enablers: Protecting a cloud environment with Google security solutions also enables security as a business enabler, allowing accelerated business agility due to increased operational efficiency and reduced cost.
Overall, the SRF suits organizations who are still early in the adoption journey and are looking for a risk-based approach to migrate to Google Cloud to operate workloads aligned with Google Cloud security and resilience best practices. The SRF checklist and SRF discovery tool are handy tools for kick-starting the secure adoption journey to Google Cloud and are free of charge.
While the SRF helps with securing the cloud foundation, this does not include specific guidance related to generative AI. To this end, Google released the Secure AI framework (SAIF) in 2023. This provides guidelines to mitigate risks associated with AI systems and helps secure GenAI applications.
One key element covered by SAIF is the expansion of strong security foundations within the AI ecosystem. Often, these foundations lie in the cloud, making it important to address this aspect and ensure the basics are correctly established for underlying AI ecosystem components. For a deeper dive into AI ecosystem security, read Eviden’s Digital Security Magazine article about how you can establish a secure foundation for GenAI applications.

The power of partnering: Eviden and Google
Eviden is a leading Managed Security Service Provider (MSSP) with 17 global security operations centers (SOCs) and 6,500 security professionals, processing 30 billion events daily. We aim to help customers innovate and secure assets on Google Cloud.
Customers can now benefit from a powerful partnership between Eviden and Google to provide comprehensive managed security services for protecting hybrid and multi-cloud environments, including for GCP.
Eviden is a Google managed service partner (MSP) with 11 partner specializations and 3 MSP competencies, as well as a three-time Security Partner of the Year. This translates to real-world results. For example, Dentsply Sirona leverages Eviden’s MDR service powered by Google SecOps to proactively combat threats. Eviden has also designed and implemented a Secure Cloud Landing Zone for Accor, safeguarding critical payment data and ensuring PCI compliance and setting a new benchmark for hospitality industry standards.
Want to learn more about how Eviden can help your organization increase the speed of your migration to Google Cloud while enhancing your security?
- Visit our website or contact one of our experts today.
- Learn more about our expertise as a Google MSP.





