Not to be all doom and gloom, but what would you do if your bank’s systems suddenly went offline for a few days? My world would probably stop immediately. Does anyone still carry cash or checks? Digital payments and online financial services make common daily activities possible. This thought experiment shows that the resilience of the financial sector is more critical than ever.
Enter the Digital Operational Resilience Act (DORA), a pioneering regulation by the European Union designed to fortify the financial industry’s defenses against a growing array of digital threats. Covering a vast network of over 22,000 financial entities and their critical information and communications technology (ICT) third-party service providers, DORA sets rigorous standards for safeguarding, responding to and recovering from ICT-related incidents.
With the compliance deadline fast approaching in January 2025, the pressure is mounting. Non-compliance is not an option. The stakes are high, with severe penalties, operational restrictions and significant reputational damage on the line.
This blog post delves into the real challenges of DORA implementation and offers insights on navigating the path to effective compliance. I hope it helps your organization to not only meet regulatory expectations but also enhance its operational resilience.
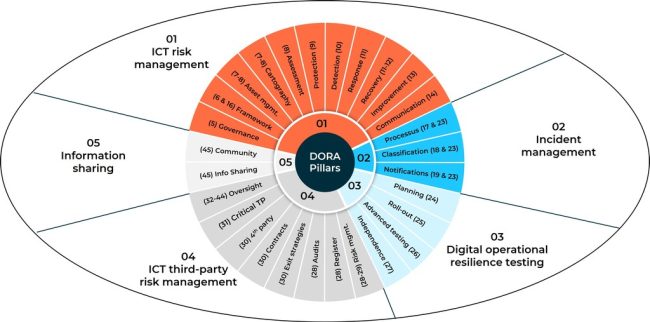
Key groups of DORA requirements
As detailed in the final text for DORA, there are 5 key groups or pillars of requirements:
- ICT risk management framework (Pillar 1): Chapter II, articles 5-16
- ICT-related incident management (Pillar 2): Chapter III, articles 17-23
- Digital operational resilience testing (Pillar 3): Chapter IV, articles 24-27
- ICT third-party risk management (Pillar 4): Chapter V, articles 28-30, plus oversight framework with articles 31-44
- Information sharing (Pillar 5): Chapter VI, article 45
An alphabet soup of regulatory guidance
Apart from the main DORA regulation, there are also lower-level guidance documents published by the three European Supervisory Authorities (ESAs):
- European Banking Authority (EBA)
- European Insurance and Occupational Pensions Authority (EIOPA)
- European Securities and Markets Authority (ESMA)
The ESAs’ guidance documents are called Regulatory Technical Standards (RTS) and Implementation Technical Standards (ITS). Detailing some of the requirements of DORA, they were published in two batches (first batch and second batch). As the guidance contains various topics for several articles, this blog post will focus only on requirements described in the DORA regulation.
Which of the requirements are real challenges?
In our view, the requirements that will be the most challenging and demanding to address are:
- Digital Operational Resilience Testing (Pillar 3)
DORA introduces new obligations for establishing, maintaining and reviewing a comprehensive digital operational resilience testing program, which is a key part of the ICT risk-management framework outlined in Pillar I. This program must encompass both cybersecurity and resilience testing, extending beyond traditional continuity and penetration tests. The real challenge is implementing a cohesive framework that integrates information security, cyber resilience, disaster recovery and cyber recovery.
In addition to conventional security testing, advanced testing, known as threat-led penetration testing (TLPT), is required every three years under regulatory oversight. TLPT is based on methodologies like Critical National Infrastructure Banking Supervision and Evaluation Testing (CBEST) and European Union threat intelligence-based ethical red-teaming (EU-TIBER).
TLPT differs from standard penetration tests by including threat intelligence and alignment with authorities on relevant attack scenarios. The first phase of TLPT, preparation, involves assessing risks in the institution’s live systems and defining a white team, along with the red and blue teams. Scenario-based tests in Phase 2 then identify vulnerabilities within the context of a threat scenario, offering a comprehensive cyber risk analysis in Phase 3.
- Third-Party Risk Management (Pillar 4)
Pillar 4 of DORA requires substantial effort to integrate the ICT third-party risk strategy with the overall ICT Risk Management Framework (Pillar 1). This integration must be maintained and reviewed regularly. Financial institutions must also keep an updated inventory of all ICT third-party service providers, which may require renegotiating contracts to meet DORA standards. In some cases, this could mean reducing dependence on or switching providers to address concentration risks.
Additionally, institutions must assess the impact of subcontractors on critical functions. For less experienced organizations, identifying and managing these critical functions can be particularly challenging.
- Interpretation of critical and important functions (Pillars 1 to 4)
DORA defines ‘critical functions’ based on Article 2(1), point (35), of Directive 2014/59/EU, which establishes a framework for the recovery and resolution of credit institutions and investment firms:
It says, “‘critical functions’ are activities, services or operations, the discontinuance of which is likely in one or more Member States, to lead to the disruption of services that are essential to the real economy or to disrupt financial stability due to the size, market share, external and internal interconnectedness, complexity or cross-border activities of an institution or group, with particular regard to the substitutability of those activities, services or operations.”
From the above definition, it is evident that conducting a business impact analysis (BIA) as part of the business continuity process is essential for determining critical or important functions.
DORA compliance: An evolution or a revolution?
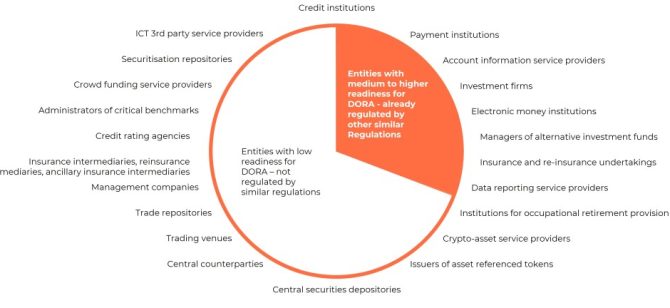
DORA’s scope, as outlined in Article 2.1 points (a) to (t) (see Fig. 2 below), includes both highly regulated, mature entities like banks, insurers and investment funds (marked in orange), and less regulated, less mature entities (marked in white).
For the less regulated entities, identifying critical and important functions poses a greater challenge. They must develop robust governance and operational resilience policies, procedures and documentation, and implement necessary safeguards and controls. For such entities, this process may represent a revolutionary transformation.
Is there a revolution for more regulated entities?
Yes, even highly regulated entities face significant changes. They must adopt new practices such as TLPT under Pillar 3 and enhanced third-party risk management as outlined in Pillar 4. This can be particularly challenging for larger organizations that need to compile a comprehensive inventory of ICT service providers and assess their subcontractors. Managing this task becomes complex, especially when dealing with a large number of suppliers (sometimes over 100) that require thorough inventory and evaluation.
Attain alignment. Sustain compliance
To achieve full compliance efficiently and at minimal costs, financial institutions should seek expert guidance from external partners. These experts provide valuable insights, best practices and objective assessments, helping navigate complex regulatory requirements while enhancing cybersecurity.
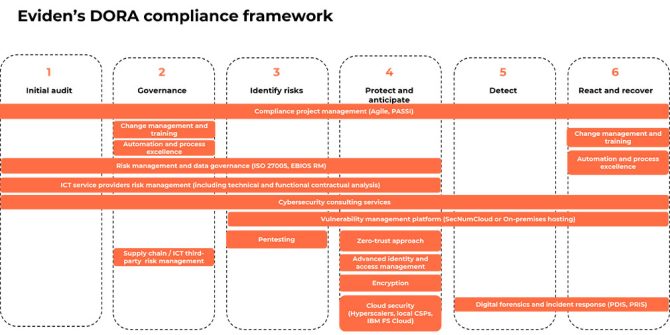
Eviden recommends a structured six-step approach to achieving and sustaining DORA compliance:
- Initial audit (compliance gap assessment): Assess the existing cybersecurity posture, processes and defenses with regard to DORA requirements; aiming to discover potential compliance gaps.
- Set up a governance structure: Establish or align with (if already existing) a governance framework to support the DORA compliance program, incorporating change management, employee training and automation to ensure lean, cost-efficient procedures. Here, it is important to integrate with an already existing industry governance framework, like EIOPA’s system of governance for insurers.
- Identify risks: When potential or real DORA compliance gaps are identified, they need to be understood in the context of related business and cyber-resilience risk scenarios. This brings much more value than you’d get from simply checking the gaps.
- Protect and anticipate: Address gaps and related risks by implementing various protective measures, starting from adjustment of documentation through to upgrading specific areas of cybersecurity or resilience (e.g., encryption, vulnerability management, identity and access management, zero-trust security, etc.).
- Detect: Implement triggers and detection controls to receive early warning signals on deviations from the normal effectiveness of your safeguards related to compliance benchmarks.
- React and recover: Establish reactive and recovery measures like procedures, including periodic testing to document the prescribed reaction to and/or recovery from an incident. And be sure to train staff on expected behaviors to minimize damage and secure operations.
It’s a long-term commitment
Achieving DORA compliance is a multifaceted challenge requiring strategic planning, significant investment and continuous effort. By understanding the critical requirements and implementing a risk-management framework, financial entities can enhance operational resilience, protect against emerging threats and build stakeholder trust. But mind the proportionality principle and keep your framework scoped to your needs.
For heavily regulated entities like banks and insurers, this process evolves their existing security procedures. Less regulated entities may require more revolutionary transformations. Early planning, investing in technology and expertise, and fostering a culture of compliance are key to sustaining long-term compliance and ensuring the financial ecosystem’s stability and security.
Learn more about Eviden’s Financial Services Security and Compliance expertise.
Explore the latest cybersecurity trends in our Digital Security Magazine.
Connect with me to discuss your organization’s approach to DORA compliance and how you can adopt and adapt faster.