A CISO’s inbox is like a battlefield with a massive load of data and information on emerging threats, new vulnerabilities, changes in regulatory requirements, news on cyberattacks and the like. This daily overdose makes it difficult to sift through important news and critical cybersecurity issues that need immediate attention.
How, then, can CISOs cut through the noise and develop a strategy that truly protects their organization to keep it secure 24×7?
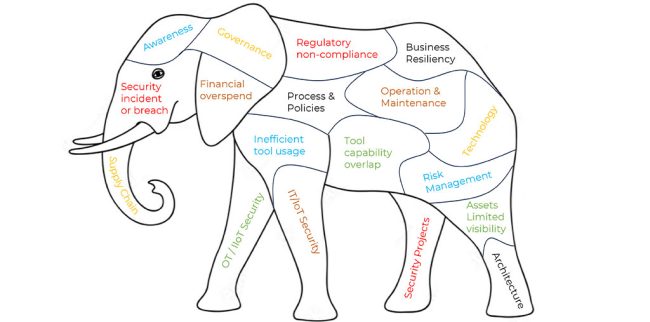
Let’s deal with the elephant in the room
In the face of overwhelming cybersecurity challenges, a practical and adaptable approach is essential. Imagine the cybersecurity spectrum of possible activities in your scope is an elephant — a huge animal that you are trying to measure and understand. As you map the different aspects of it, the entire picture comes to life, giving you an accurate idea of the necessary activities for airtight cyber health. This assessment can pave the way for a holistic overview of your cybersecurity management.
After planning the best route on a cybersecurity roadmap, i.e. from where you are to where you want to be, you have to navigate yourself wisely and cautiously on that course to eventually reach the target cybersecurity posture. Incremental enhancement is crucial, based on organization-specific prioritizations of activities.
This is the core of the strategy.
Now, you can approach the elephant one piece at a time with the strategy of “PRIORITIZE, FOCUS, CHECK.”
Prioritize and focus
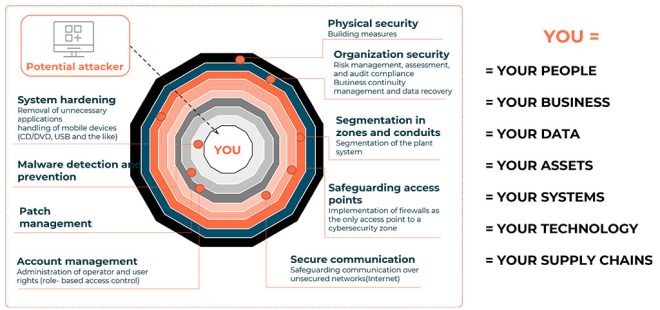
Stay focused and ensure you keep what matters the most at the center of your attention. Referring to Figure 2, YOU are where the organization’s business-critical assets lie, and this serves as a filter to develop a good cybersecurity roadmap. Using this, you can prioritize critical areas and make a SMART Investment in cybersecurity.
Verify how protected YOU are by proactively engaging stakeholders. Use tabletop exercises or penetration testing to assess your cybersecurity investment needs and find where YOU are the most vulnerable. There are three axes of your cybersecurity prism through which threats and risks need to be checked for adherence and impact.
This is vital to establish what is urgent and critical:
- Regulatory compliance: Monitoring upcoming and new regulations for your specific industry can be achieved in several ways. Regardless of your industry, consider subscribing to regulatory updates from relevant bodies, associations, and legal firms to stay informed about changes. Engage with industry networks by participating in panels, workshops, and webinars to gain insights into upcoming regulations and compliance best practices. Implement governance, risk, and compliance (GRC) platforms with AI-based tracking and automated policy updates to remain agile and responsive to regulatory shifts. Consult with legal advisors specializing in your industry for detailed interpretations of new regulations and their impact on your business. Periodically review and assess your compliance risks to proactively identify and address potential vulnerabilities.
- Tailoring cybersecurity referential architecture archetypes and cybersecurity design principles: Begin by identifying and cataloging all organizational assets, including hardware, software, data, and network components, using automated tools for accuracy. Understand asset interactions and dependencies by creating detailed diagrams or maps, which help identify critical failure points and areas needing enhanced security. Evaluate existing security controls through regular audits, vulnerability assessments, and penetration testing to determine their effectiveness and identify gaps. Collaborate with departments and stakeholders to align security measures with business operations. Based on these insights, develop and implement tailored security measures, adopting best practices from frameworks like NIST, ISO 27001, and IEC 62443. Establish a continuous monitoring process to track changes in asset inventory, interdependencies, and security controls, and regularly update your cybersecurity architecture and design principles to adapt to new threats and business needs.
- Vulnerability and threat landscape: Continuous screening for vulnerabilities of your assets and new threats or vectors is critical. Utilize advanced SIEM and EDR tools for real-time network monitoring to detect unusual activities and potential threats. Conduct regular vulnerability scans and penetration tests to proactively identify and address system weaknesses. Integrate threat intelligence feeds into your security operations for up-to-date information on emerging threats and attack vectors, allowing you to adjust defenses accordingly. Automate, where feasible and aligned with business and risks, repetitive tasks like patch management and incident response to maintain a consistent security posture and reduce human error. Collaborate with MSSPs or cybersecurity experts for 24/7 threat monitoring and specialized support. Ensure your security team receives regular training on the latest threats and mitigation techniques and conduct awareness programs for all employees to recognize and respond to potential threats.
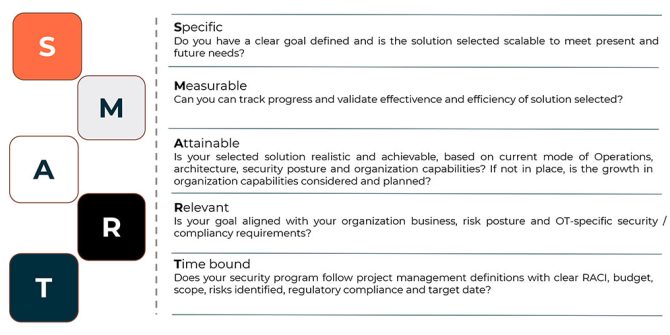
Invest SMART
Buy-in is crucial, hence use the S-M-A-R-T approach to justify the cybersecurity business case for your roadmap.
Setting the strategy
Decide where YOU want to be, based on where YOU already are, while ensuring you derive optimal value throughout the journey.
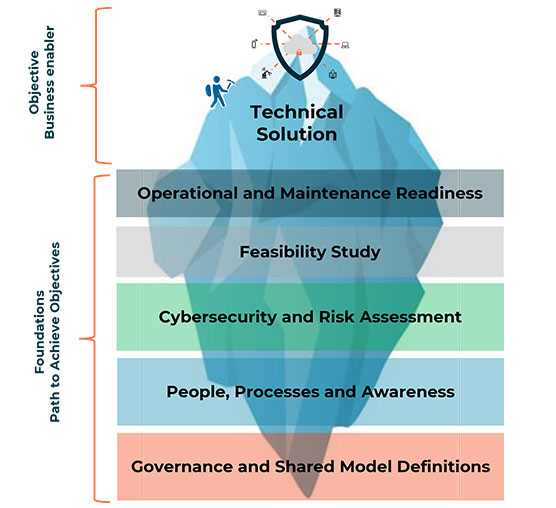
The above-mentioned elephant analogy develops a firm foundation for an organizational cybersecurity strategy, aligned with business goals and risk assessment. This robust strategy, that supports you in building a cybersecurity posture, is the one that needs to dive beyond a technical solution to assess the various elements of your cybersecurity status, as presented in Figure 4. Only then will it propel your organization to the target cybersecurity posture.
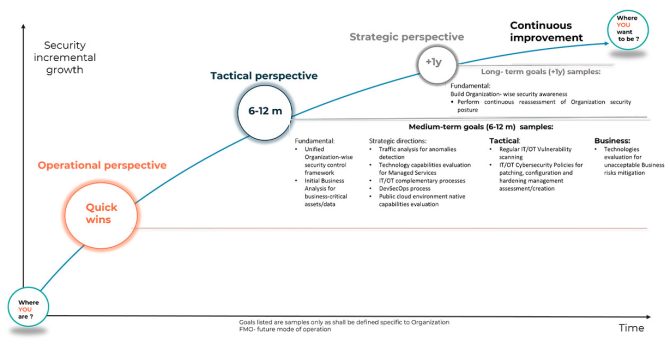
The best-suited roadmap is one that navigates smartly with business value at the horizon, within the agreed budget, scope and timeline. The cybersecurity roadmap depicted in Figure 5 below illustrates how a strategic approach can guide an organization from its current state to a desired level of IT-IoT-OT security operational readiness. It’s a journey of continuous improvement, with a focus on achieving both quick wins and long-term goals.
The roadmap is divided into three perspectives:
- strategic (long-term),
- tactical (medium-term),
- and operational (short-term).
Each perspective encompasses fundamental security principles, as well as goals and actions that align with the organization’s unique business needs and risk profile.
It’s important to note that this is just a sample roadmap. Every organization is different, and your roadmap should be tailored to your specific circumstances.
Eviden’s team of cybersecurity experts are catalysts in helping global leaders achieve their cybersecurity goals and can help you develop a customized roadmap that addresses your organization’s unique challenges and guides you towards a more secure future.
Journeying towards a common goal: Let’s climb together
Eviden’s proven Prioritize, Focus, Check approach offers CISOs a clear strategy for managing their security challenges and efforts, ensuring that resources are assigned towards the most pressing risks, threats and vulnerabilities. Our team of global cybersecurity advisors and cross-functional experts combine their experience and expertise with your business needs, providing future-ready advisory and consulting guidance and support to achieve your goals.
Reach out to either of us to discuss how cybersecurity trends are shaping the ecosystem and how they may be impacting your industry.
Learn more about how Eviden’s innovative approaches can be customized for your industry and your organization with OT security solutions.