Cyberattacks are often motivated by financial gain or political principles. A company’s information that has been leaked in a data breach may be held for ransom and/or sold on the dark web, while geopolitical events can influence a malicious group’s targets.
With the ever-changing nature of threats, Blue Teams are now more proactive in their surveillance, and they depend on reliable cyber threat intelligence (CTI) for this.
The four types of cyber threat intelligence
Comprehensive CTI comprises of four interlinked types of intelligence:
- Strategic intelligence: This type of intelligence provides a larger view of the cyber threat landscape. It helps senior leaders understand long-term trends, potential risks, and the motivations behind cyberattacks. With this information, businesses can shape their security strategies and anticipate threats before they become critical issues.
- Tactical intelligence: Tactical intelligence focuses on the specific tools and methods that attackers use. It gives security teams insights into how hackers operate, allowing them to build better defenses against known tactics and techniques. This kind of intelligence is practical for day-to-day threat detection and response.
- Technical intelligence: Technical intelligence deals with the raw technical details of a cyberattack, such as IP addresses, malware signatures, and malicious URLs. It’s the kind of data that security systems can use to block or detect threats as they happen. This intelligence is often highly specific and used for automated responses.
- Operational intelligence: Operational intelligence is all about what’s happening right now. It provides timely, actionable information on current threats targeting your organization. Security teams use this to respond to active incidents or prevent attacks that are imminent.
Figure 1 below examines how these are linked to each other.

Stakeholders in the CTI ecosystem
Now, let’s explore the different types of CTI in detail and the stakeholders involved at each stage.
Strategic intelligence is for stakeholders and high-level management. Although strong technical knowledge is not required, an understanding of the potential risks and impacts of cyber threats and attacks on companies is crucial. This type of intelligence influences company policies and publications in cybersecurity and helps guide companies towards more secure infrastructure.
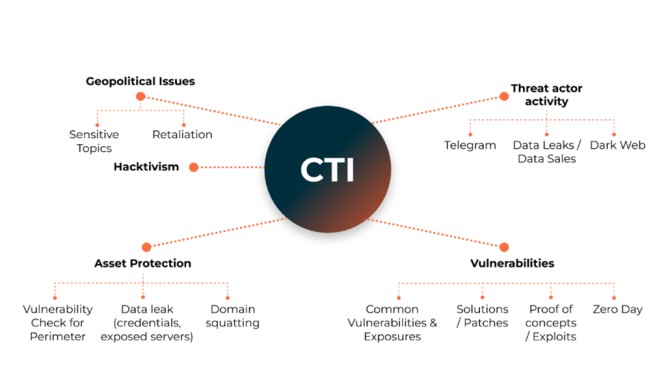
From technical and contextual perspectives, CTI searches for the following:
- Vulnerabilities in products used by organizations and their corresponding solutions
- Successful exploits of these vulnerabilities and preventive measures
- Data breaches and/or the sale of personal or professional data on the dark web
- Geopolitical issues, such as state-sponsored threat actors that may aim to destabilize organizations or countries
- Hacktivism
- Direct and indirect threats to organizations
- Incentives for malicious hacking, as observed on platforms like Telegram
The search results provide the analyst with tactical intelligence by identifying the tactics, techniques and procedures (TTPs) used by threat groups. TTPs portray a contextual picture of threat actors and the threat landscape. In addition, Indicators of Attack (IOAs) help detect and understand an attacker’s objective, methods, and behaviors. This may take the form of spear-phishing, a targeted phishing email, methods of persistence once the system has been compromised, or exploiting a zero-day vulnerability.
In terms of incident response, CTI also provides security analysts with a more enlightened picture and faster reflexes, especially when time is of the essence.
During an attack, evidence of malicious activity allows the analyst to assess Indicators of Compromise (IOCs). These may be IP addresses, hashes, domain names, phishing email content and/or malware samples. These IOCs are part of technical intelligence and should be exploited quickly as they help mitigate and may even reduce the scope of an attack. This may be possible by blocking a malicious IP, adding a hash to a blacklist, or reporting a domain name.
Finally, operational intelligence brings together elements such as motive, timing (maybe before an important event), execution of an attack, or current exploit trends. This information can be found on X (formerly Twitter) feeds, Telegram or after infiltrating a threat group’s online discussions.
Overall, different types of CTI are interlinked and offer a solid foundation for Blue Teams.
Benefits of threat intelligence
No cybersecurity strategy or solution can guarantee complete security but it can reduce the risk and impact of a cyberattack by enabling the Blue Team to anticipate potential issues. In addition, when confronted with an attack, CTI program results go a long way in fortifying your defence and improving incident response.
Threat intelligence also has financial benefits. After all, awareness can lower the financial impact of an attack. If an analyst notices and understands a vulnerability in a company’s server, it can be patched before an attacker notices and exploits it.
If a system has been compromised, an attacker can steal sensitive information, install malicious software, obfuscate their presence, escalate privileges and gain access to other parts of the network.
A CTI analyst can help reduce the dwell time — the time spent by an attacker in the system — by tracking the attacker’s TTPs and IOCs. By providing security engineers with this information, the analyst can also reduce impact to the system.
Challenges in managing CTI
CTI does come with some challenges.
Providing accurate and usable data includes ensuring data has a correct timestamp, has not been tampered with, and comes from a legitimate source. If sources are not vetted properly, false positives can be common while inaccurate data can generate alert fatigue. This can be mitigated by using machine learning tools to filter the data at an early stage. In addition, CTI tools can be selected based on sector specializations and market reputation, providing more accurate and exploitable data.
Another challenge is a lack of sufficient and effective resources, including time, financial support, and training. An effective analyst would have certifications that lead to a special skillset and domain expertise. This experience would guide them in their recommendations and actions for a company’s CTI.
Integrating threat intelligence into your security posture
CTI can also be based on Open Source Intelligence (OSINT). This can be accessed through X posts, press releases from cybersecurity companies, open-source tools such as Virus Total or Cisco’s Talos Intelligence, Telegram channels where malicious actors announce attacks, allegiances, classes, and memberships. All this information is easily accessible and does not require an additional fee for basic use of the platforms. For companies with a smaller budget, this can be a first step.
For companies with bigger budgets, specialized OSINT tools, such as Threat Fusion or Recorded Future, can be integrated into their security posture. Before integrating threat intelligence, it is recommended to critically evaluate a CTI feed to determine accuracy, timeliness, and how a feed can be tweaked to reduce noise and provide a majority of true positives.
Another way to improve awareness of different threats is to be a part of a community of organizations that agrees to share their CTI. An association of different national Computer Emergency Response Teams (CERTs) can collaborate and consolidate their CTIs in a secure platform with strict Traffic Light Protocols (TLPs). This platform can be a quick and easy way to share different threat intelligence such as TTPs and IOCs that can help two different companies facing similar types of attacks.





