It is said that France is the country with 400 kinds of cheeses and 400,000 laws. But you can find as many cheeses and laws elsewhere in the world. European legislation and EU regulations are no exception. With more than 10 regulations planned on digital matters between 2024 and 2027, the EU digital package constitutes a cheese factory all by itself!
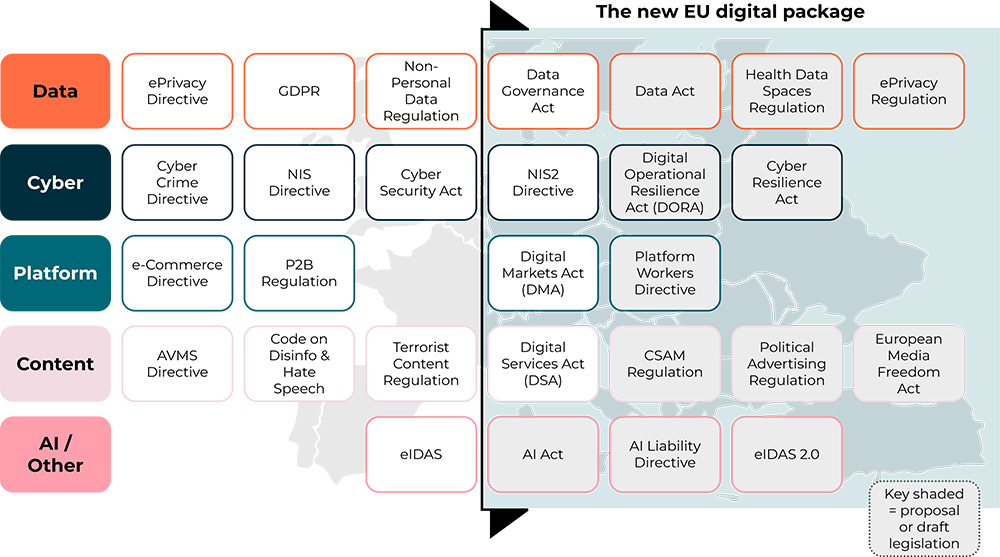
The EU Digital Package: An intensification of regulations and recommendations
Almost every country in the world is focused on strengthening their digital sovereignty and cyber defense in preparation for what is referred to as a high-intensity war, where adversary powers would target IT systems of critical infrastructure operators or essential service providers first. The NIS and NIS2 directives for Member States aim to unify these national laws voted locally across Europe.
In addition to this supranational regulatory framework, there are also:
- Sector-specific regulations such as those in healthcare, telecommunications, environment, and R&D
- Soft laws consisting of recommendations and cyber hygiene guidelines from regulatory authorities and national security agencies that you are not to disregard
- Contractual commitments like the Security Assurance Plan and SLA, ruling the relation between an organization and its partners, clients or suppliers
In the public sector, regulations proliferate from various governmental and interministerial bodies, including IT security policies, administrative circulars, and mandatory instructions for public officials.
Towards more flexible risk-based frameworks
A shift towards a new way of legislating has emerged as a key guiding principle while navigating this complex, ever-evolving regulatory landscape. This next generation of regulations embrace a risk-based approach, designed to be pragmatic and adaptable. Aware of the rapid pace of technological advancement, these regulations steer clear of rigid, technical prescriptions that quickly become outdated, aiming instead to provide a flexible framework that stays relevant in the face of constant innovation.
The first regulation to exemplify this new approach was the 2002 Sarbanes-Oxley Act, particularly Section 404, which requires companies to implement internal controls and demonstrate their effectiveness. This law introduced two groundbreaking concepts that have become widely adopted:
- A risk-based approach – Organizations have the flexibility to determine their own technical and organizational measures, but they also need to—
- Be proportionate to the risks associated with their activities, and
- Ensure compliance with the core legal principles.
- The principle of accountability and the reversal of the burden of proof – It is the responsibility of the organization to prove to the regulatory authorities that the security measures in place are both adequate and effective.
The GDPR, the AI Act and other anti-corruption legislations have adopted these principles as their foundational pillars and methodologies.
How state of the art reverses the burden of proof
Recommendations from data protection authorities, national cyber security agencies, and even civil courts consistently emphasize the concept of state of the art. The French Data Protection Authority (DPA) describes it as “a set of best practices, technologies, and publicly accessible reference documents related to the security of information systems, and the information that can be evidently derived from them.” This obligation to remain at the cutting edge of technological and security standards also brings with it a reversal of the burden of proof, where a presumption of non-compliance requires organizations to demonstrate they have met this heightened obligation of means (best efforts).
Consequently, having internal legal experts is no longer sufficient to ensure regulatory compliance. They must be joined by risk managers to identify and assess risks and threats, and by technical experts and Chief Information Security Officers (CISOs) who must continuously maintain their knowledge at the cutting edge. Just as importantly, decision-makers must prioritize governance, risks and compliance (GRC) concerns and allocate sufficient resources to achieve compliance.
Choosing the right assessment methodology
To aid this, risk managers and CISOs have access to numerous risk assessment methodologies. Impact assessments (like DPIAs)are core to both GDPR and the AI Act and focus on analyzing threats, vulnerabilities and risks, and assessing their likelihood and potential impact.
In the context of cybersecurity, various methodologies are available, each following similar steps:
| EBIOS RM | Often preferred by organizations under French regulations |
| ISO/IEC 27005 | Aligns well with other ISO standards
Adaptable to organizational needs |
| OCTAVE | A business-oriented, participative approach that empowers internal teams |
| NIST SP 800-30 | Detailed and regularly updated
Widely used in both public and private sectors in the US |
| FAIR (Factor Analysis of Information Risk) | Focuses on risk quantification
Especially useful for financial decision-making |
| CRAMM (CCTA Risk Analysis and Management Method) | A detailed method often applied within the British public sector |
| MAGERIT | Widely used in Spanish-speaking countries
Suitable for large organizations |
The choice of a risk assessment methodology depends largely on the organization’s context, needs, and requirements. However, the first challenge is often cultural, embracing a risk management mindset in an environment where the boundaries between what is allowed and what is prohibited are increasingly blurred. It is an organization’s responsibility to decide how to protect its IT assets and the data they handle with the understanding that it will be held accountable for its decision if something goes wrong.
Ultimately, compliance hinges on an organization’s ability to demonstrate that risks have been properly assessed, and the unacceptable risks mitigated. Can you?





