The paradox: More regulations, but also more breaches!
In recent years, we have seen new cybersecurity regulations and laws being adopted, such as GDPR, NIS2, and DORA. However, we can observe a curious trend. Despite more regulations, data breaches continue to rise. According to annual data breach research, data breaches in the U.S. increased by 68% compared to previous years. Meanwhile, since the GDPR’s implementation in 2018, over 2,000 fines totaling more than €4 billion have been issued, according to GDPR Enforcement Tracker. Furthermore, data privacy research suggests that, on average, data breaches take over 113 days to detect, with the average time between breach detection and consumer notification exceeding 133 days.
This raises the question: Do regulatory requirements bring real benefits to cybersecurity, or would breaches be even higher without them? Or do data breaches occur regardless of regulations?
In this article, we will take a closer look at the correlation between cybersecurity regulations and data breaches.
Regulatory fines vs. Data breaches: Coincidence or correlation?
Let’s start by asking a bold question: Is there an actual correlation between the rise in regulatory fines and the growing number of data breaches?
To answer this, we need to look at the number of reported data protection incidents in Europe. Cyber Crime & Security suggests that the number of reported incidents has surged. However, this increase does not necessarily mean that there are more security incidents, but rather that breaches are being identified and reported more frequently compared to regions without such strict reporting rules.
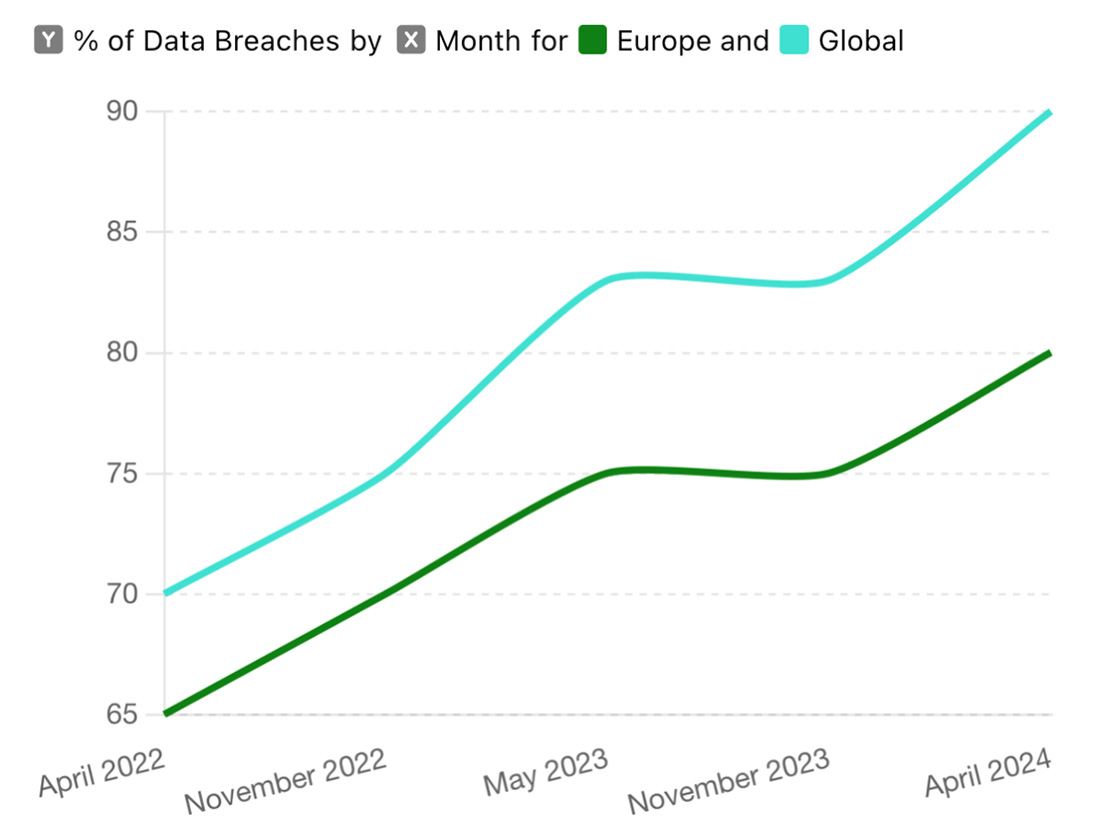
From this statistic we can conclude that despite the global rise in major security incidents, Europe’s figures are comparatively lower. This also reflects the overall impact of regulatory enforcement on data breaches. But how effective are mandatory breach notifications really?
Mandatory breach notifications and their (modest) impacts
The next pressing question is to see whether post-breach notifications are effective. In exploring the GDPR’s impact, we’ve noted a clear improvement in how seriously European organizations take data security since its adoption in 2016.
Studies, such as the Cisco Data Privacy Benchmark Study, suggest that GDPR has indeed motivated controllers to enhance their data security practices by mandating post-breach notifications. According to the report, over 80% of organizations state that complying with data privacy laws has improved their overall cybersecurity posture and reduced privacy-related risk.
However, to understand whether this also extends to breach notifications under GDPR is a bit more challenging. Research by Bisogni (2020) indicates that mandatory breach notifications lead to only modest improvements in data security practices. This is supported by research examining the costs and causes of cyber incidents, which suggests that mandatory breach notifications bring only modest improvements in data security practices, depending on the strictness of the rule. The study concludes that mandatory breach notifications reduce identity theft by about 10%. However, when stricter rules require disclosure for low-risk breaches, the reduction is only ~4%.
This marginal decrease shows us that mandatory notification alone is not sufficient to drive significant changes in organizational security practices. Also, this is also not effective in preventing future breaches. So how is GDPR improving data security and privacy?
The conundrum of compliance
The complexity of GDPR compliance presents several challenges that can be seen as the compliance conundrum.
First, inconsistent enforcement across EU member states allows companies to evade strict penalties based on location, undermining the regulation’s effectiveness. Small- and medium-sized enterprises face disproportionate costs to meet GDPR requirements, while larger companies can more easily absorb these expenses.
Moreover, the intricate nature of GDPR regulations can increase the risk of data breaches, as organizations may struggle with complex compliance demands, potentially leading to unintentional breaches.
Industry standards like ISO 27001 emphasize formal security requirements but lack detailed implementation guidance. This lack of clarity leaves room for interpretation and may not effectively enhance data security and privacy practices.
Therefore, while compliance with regulations like GDPR is important, it is simply not enough to make an impact on the overall security posture. As the saying goes, “You can be compliant with a security standard or regulation and still not be secure.”
Strong data security and privacy require going beyond the minimum compliance requirements to adapt data security and privacy measures to evolving threats.
Compliance alone is not enough!
Despite increasing cybersecurity regulations like GDPR, DORA and NIS 2, data breaches keep rising. While these regulations have raised awareness and led to some improvements, the security outcomes are only modest. This is because organizations focus more on ticking compliance boxes than on proper security improvement. Breach notifications and fines push organizations to act, but the impact is minimal.
Complex regulations and inconsistent enforcement further limit their effectiveness. Meeting legal requirements doesn’t guarantee an improvement in the cybersecurity posture, as shown by modest improvements despite mandatory breach notification.
To truly reduce breaches, organizations need a proactive approach —adapting to risks and implementing security measures beyond mere compliance. The goal must be real protection, not merely ticking the boxes of regulatory controls!





