2024 is the year data sovereignty takes the spotlight.
This year, Microsoft publicly admitted to Scottish policing bodies that they cannot guarantee sensitive law enforcement data will remain in UK, as mandated by Part 3 of the Data Protection Act (DPA) 2018, despite long-standing public claims to the contrary[1]. Similarly, Google sent emails to its customers during the summer, stating that they “may need to share confidential information with the US government authorities when legally required”.
This ends the ‘we did not know’ period and highlights the following (rather disconcerting) admissions for several countries equipped with data privacy regulations:
- Data may be transferred and processed overseas, even when the Cloud provider claims otherwise.
- Data processing agreements may not fully cover the country’s specific data protection requirements.
- Case-by-case management has been rendered incompatible by industrialization. Data protection in data ecosystems is probably heterogeneous with Cloud providers applying specific measures only upon request.
- Data controllers are responsible for determining the relevant security and data sovereignty controls to be compliant with their regulations. This was the position of Microsoft lawyers.
- Data at rest and data in transit security are foundational but might not be sufficient when data processing is hosted by a third-party.
Concerned organizations that continue to use these services are knowingly breaking existing data privacy laws, such as the UK DPA. So, how can they ensure compliance?
Reducing risks with privacy enhancing technologies (PETs)
Fortunately, emerging privacy-enhancing technologies (PETs) are offering certain levels of cryptographical and mathematical guarantees for data in use. This ensures confidentiality and integrity to meet data privacy requirements and reduce data processing security risks.
The GDPR and EUDPR, designed to protect the processing of personal data by EU institutions and agencies, have been providing recommendations for data privacy[2]. More and more regulations are now referring to PETs as recommended solutions, such as the amendment to the Regulation (EC) 223/2009 adopted in March 2024 by the European Parliament on European Statistics. The agreed legal text makes explicit reference to privacy enhancing technologies when it comes to “secure infrastructure […] based on technologies that are specifically designed to comply with [GDPR and EUDPR]”.
Managing and mitigating risks in the data sovereignty ecosystem
PETs can contribute to reducing risks to data sovereignty in various ways and to various extents. Here are some leading examples:
| Technology | Actions | Results |
| Trusted execution environment (TEE) | TEE isolates your data and code in a secure enclave within untrusted environments (potentially provided by foreign Cloud providers subject to extra-territorial obligations). | You reduce the attack surface but still need to rely on some residual implicit trust about the TEE implementation done by the server manufacturer. |
| Fully homomorphic encryption (FHE) | FHE ensures data is always encrypted, even in RAM and CPU, never exposing it to the infrastructure provider. | Guarantee that you are the only organization able to read the data in cleartext. |
| Secure Multi-party Computation (SMPC) | SMPC enables collaborative computations on data without sharing, moving or exposing your sensitive source data to other data controllers outside your borders at the entity, enterprise, national or transnational levels. | You reduce the sensitivity of shared data without negatively impacting your contribution to collaborative work. |
| Synthetic data and differential privacy | This generates respectively mimicked or noised data in cloud environments with third parties. | You can compliantly share data without exposing real sensitive information. |
| Secure federated learning | Training a shared model locally and aggregating it centrally with data privacy mechanisms guarantees your granular data will not be traceable. | You eliminate the need for your data to leave your direct control (within your borders). |
Fig 1: Leading PETs, what they do and how they are managing or mitigating risks
In addition to the above, incorporating privacy-by-design embeds privacy protections into systems from the outset and privacy-by-default ensures the strictest privacy settings are automatically applied. With these, PETs can minimize data exposure and ensure compliance with data privacy frameworks.
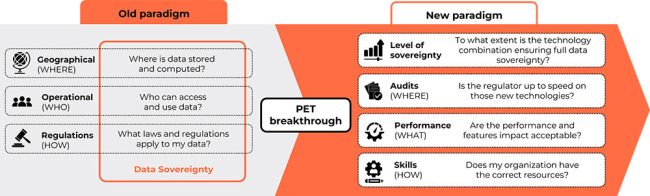
A paradigm shift with PETS
With PETs emerging, data sovereignty questions extend beyond data localization and access. Data can remain always encrypted, including during computation, with encryption keys held solely by the data controller. And the service can still be provided by the service provider (Cloud provider or other third party).
So, is everything for the best in the best of all possible worlds? Of course not, with properly implemented PETs, we do face a new paradigm in terms of possible negative impacts to balance out, but they now differ from what we used to face.
Here are several questions to answer in assessing the PET implementation:
- What is the specific data scope that needs to be protected by PETs, and from whom?
- What is the level of data sovereignty to be achieved?
- Which trade-offs are acceptable to reach the above ambition? Consider this in terms of:
- Impact on technical performances
- Implementation efforts and impact on infrastructure, data, AI/ML, and applications
- Required resources and skills, such as cryptographic and mathematical expertise
- Are there any regulatory constraints specific to the domain such as in terms of auditability?
Innovations like big data, AI/GenAI and computer vision are raising questions for regulators regarding the privacy, security and sovereignty of data, information and knowledge.
These breakthroughs are challenging the effectiveness of existing laws, and the capability of regulators to move at the right pace. Meanwhile, issues such as data breaches, government intrusion and surveillance, and a lack of transparency in service providers’ exploitation of data are threatening national assets.
At the same time, PETs are maturing. They are becoming more performant and operationally viable, with innovative solutions now available in the market to elevate privacy and digital sovereignty. For instance, some startups like Mithril Security or Inpher are offering private and sovereign alternatives to GenAI platforms, with Large Language Models running on TEE. In parallel, we can also run now AI/ML inference with FHE, having the AI model run on encrypted data and still providing the correct, expected, result.
Collaborating for a faster data strategy
In this moving regulatory and technical landscape, it is now more challenging than ever for enterprises to identify an optimum strategy and solutions to exploit its data in compliance with sovereignty rules. On top of that, they must assess operational risks – risks that only they can fully evaluate based on their unique circumstances and internal risk assessments.
This is where ecosystem collaboration is most valuable. Your trusted integration and services partner, by being technology agnostic, can efficiently guide you through the PET landscape complexity and help select the right end-to-end combination of PET technologies for your needs.
Connect with Eviden’s Cybersecurity experts for a comprehensive assessment of your business and how you can integrate privacy enhancing technologies (PETs) for faster data sovereignty solutions.
References and sources
[1] Microsoft admits no guarantee of sovereignty for UK policing data
[2] GDPR, articles 25, 5, and 32