Our traditional asymmetric cryptographic systems, (mainly RSA, ECC – Elliptic Curves – and DH – Diffie-Hellman), face a direct threat, and this may be attributed to the development of Cryptographically Relevant Quantum Computers (CRQC), capable of solving complex mathematical problems in mere moments compared to classical computers that would take millennia.
In a nutshell, the strength of these systems, which currently secure most of our communications, our confidential data and our digital transactions, relies on mathematical problems considered unsolvable at large scales, such as large number factorization or discrete logarithm computation. Indeed, the complexity of solving those problems increases exponentially when we increase the length of encryption keys. However, quantum algorithms — Shor’s algorithm in this case — enable future CRQCs to solve these problems faster and without any exponential increase of complexity when augmenting key length. The result is that once a CRQC can break traditional cryptographic schemes, doubling or quadrupling (or more) the lengths of encryption keys won’t help much, thereby rendering these protections vulnerable and potentially obsolete in the near future.
The security of these new algorithms relies on problems derived from lattice-based cryptography, error-correcting codes, and hash function security, amongst others[1]. Since 2016, the National Institute of Standards and Technology (NIST) has been conducting a rigorous process to select and standardize post-quantum algorithms. In 2022, four algorithms were selected for their robustness and efficiency: ML-KEM (Kyber) for encryption and key exchange (encapsulation), as well as ML-DSA (Dilithium), FN-DSA (FALCON), and SLH-DSA (SPHINCS+) for digital signatures. These selections mark a crucial step in preparing digital infrastructures for the quantum era.
PQC is therefore essential to anticipate the threat posed by quantum computers, as once they become operational at scale, they could compromise sensitive data stored today and decryptable within a few decades. Given this threat, PQC is becoming a fundamental pillar in ensuring the long-term security of digital systems.
[1] Those are the 3 current main families, for other families of algorithms refer to our whitepaper
Cryptographic hybridization: A crucial step toward the post-quantum era
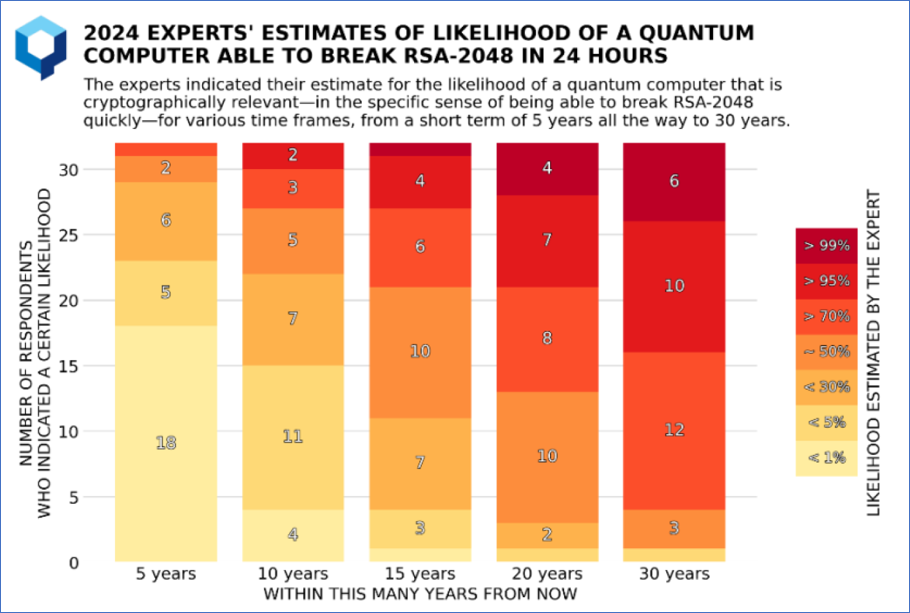
With a median forecast placing the arrival of Cryptographically Relevant Quantum Computers (CRQC) around 2034-2035, it is imperative for businesses to start preparing now. The latest quantum threat timeline report (December 2024) from the Global Risk Institute indicates that over 50% of experts estimate a greater than 50% probability that a CRQC will be operational within the next fifteen years. One of the striking conclusions of the report is that “both the opinions expressed by the experts and recent significant advances in the field suggest that a CRQC may arise faster than what some may naively expect.”
Facing this imminent threat, NIST has set strict deadlines for the use of classical algorithms, with a progressive deprecation of RSA and ECDSA (digital signatures based on Elliptic Curves) starting in 2030, followed by their total disallowance by 2035. This is an effective way of ensuring enterprises act without delay.
Although promising, most of PQC algorithms still lack maturity, and some, like SIKE, have already been compromised. Fortunately, the mathematical foundations of SIKE are very different from other PQC algorithms, meaning this attack does not apply to the other considered schemes.
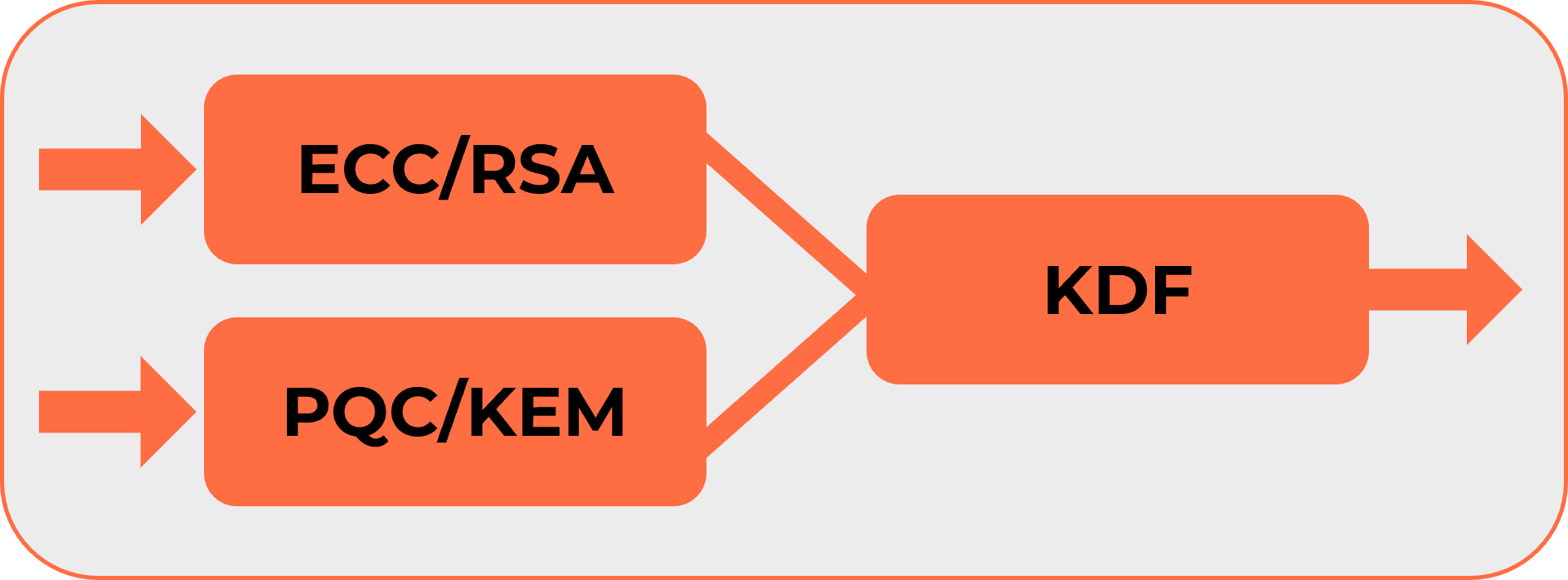
In this context, cryptographic hybridization emerges as a strategic response, reducing the risks of using immature cryptosystems while enabling a controlled transition to PQC. Cryptographic hybridization involves combining traditional algorithms, such as RSA or ECC, with PQC to create dual encapsulation, i.e. key exchange, or dual digital signatures. For example, a symmetric encryption key can be simultaneously protected by RSA and a post-quantum algorithm like ML-KEM.
Cryptographic hybridization: Safer and more agile
Additionally, in some cases, hybridization promotes a gradual transition. Instead of abruptly adopting post-quantum solutions, it allows for gradual compatibility and real-world validation, reducing technical and operational disruptions. In the cases of signatures, for example, it allows to still rely on traditional signatures (RSA or ECC) if the PQC signature is not trusted anymore, without needing a rollback.
Hybridization therefore bridges this temporary gap while preparing for the future. Several major international institutions emphasize the importance of this approach. Germany’s BSI and France’s ANSSI consider cryptographic hybridization a key step in transitioning to post-quantum algorithms. These institutions argue that this approach combines the proven robustness of classical algorithms with the emerging PQC solutions still under evaluation. They highlight the importance of dual encapsulation to ensure a minimum level of security while preparing for the future and stress the need for flexible infrastructures that support hybrid and crypto-agile solutions capable of adapting to evolving standards. European organizations ENISA and ETSI also support hybridization but insist on adhering to strict guidelines. Their goal is to avoid prolonged dependence on this temporary solution and ensure a smooth transition to fully post-quantum systems.
At the end of 2024, 18 European Union Member States signed a common statement highlighting the importance and urgency of transitioning to PQC and promoting a hybrid approach. Conversely, agencies such as the NSA (United States), NCSC (United Kingdom), and CSE (Canada) have initially been reluctant about hybridization, citing concerns such as increased system complexity, increased costs, operational risks in managing hybrid systems, and potential delays in fully adopting post-quantum solutions.
However, these reservations are evolving. The latest NIST report acknowledges the utility of hybrid systems and outlines measures to facilitate their adoption. This recognition reflects a growing awareness of hybridization’s importance in this transitional phase.
Crypto-agility: The foundation of a well-planned hybridization strategy
While cryptographic hybridization is essential, it poses performance challenges due to dual encapsulation and is only considered a transitional phase toward exclusive use of post-quantum solutions by cybersecurity agencies.
This inevitable transition to post-quantum solutions will require three successive stages:
- Exclusive use of current pre-quantum algorithms (such as RSA)
- A hybrid phase combining traditional (pre-quantum) and post-quantum cryptography
- Full adoption of post-quantum cryptography
At each stage, the priority is to ensure crypto-agility, i.e. the ability of infrastructures and systems to swiftly adapt between different cryptographic algorithms (adding new ones, disabling obsolete ones if needed, using simultaneously different algorithms in different scopes, etc.) based on vulnerabilities, technological advances and use cases. Cybersecurity agencies, such as ANSSI and BSI, also emphasize a structured and proactive approach. In their joint statement with 18 EU member states, they encourage organizations to integrate the quantum threat into their Cybersecurity risk management, to start their transition to PQC now, to have migrated systems handling sensitive data by 2030, and to adopt hybrid and crypto-agile solutions to deploy infrastructures capable of switching between classical and post-quantum algorithms for continuous compatibility.
However, it is critical to note that implementing crypto-agility with an organization’s internal business applications can be complex. It requires system modularity to avoid rigid cryptographic coding. For instance, it may be necessary to quickly switch from an algorithm like Dilithium (ML-DSA) to Falcon (FN-DSA) or SPHINCS+ (SLH-DSA) in case of compromise or discovery of new vulnerabilities.
Additionally, post-quantum algorithms are not interchangeable without consequences. Each one has unique characteristics in terms of key length, speed, and resilience. Some initiatives, such as Sandbox AQ’s “Sandwich” framework, facilitate this transition for business application developers by offering software libraries capable of automating algorithm changes. This would allow, for example, an enterprise-wide deactivation of a compromised algorithm with a single click while providing tailored customization for each application, and without having to rewrite a single line of code in the app itself. However, integrating post-quantum algorithms into current protocols remains a challenge. Standardization must extend beyond algorithm selection to include their adaptation to existing protocols and the establishment of hybrid methods for a secure and gradual transition.
Paving the way ahead with crypto-agility
Crypto-agility is much more than a technical aspect — it is a key strategy to ensure a controlled transition to a resilient ecosystem, ready to tackle the challenges of the post-quantum era. This gradual transition, beginning with hybridization, lays the groundwork for the full adoption of post-quantum cryptography and engages businesses in a proactive, flexible, and sustainable approach.