Insider threat is considered as one of the top-10 concerns in cyberspace in 2023. It is as prominent cause of concern than external attacks. According to the Ponemon Institute[1], insider threat incidents have risen 44% over the past two years. The costs per incident have also gone up more than a third to US$15.38 million. Even worse, over 70% of insider attacks are not publicly reported and thus we may not have a clear picture of how many of them occur and what damage they cause[2].
Insiders as a threat
Cyberattacks are initiated and carried out by human beings. Technology is only a tool in their hands.
With insiders are several actors meant. It refers to employees, organization members, and those to whom the organization has given sensitive information and access. But also, to contractors, vendors, custodians, or repair persons. Basically, anyone that the organization has given access to sensitive information is considered as an insider.
The phenomenon of insider threat is twofold. The insiders are considered as both non-hostile threat agents (i.e. distracted employees) as well as hostile ones (i.e. disgruntled employees).
- The insider can cause security breaches due to ignorant or careless user actions.
The negligent employee or contractor negligence, which leads to credential theft, sums up to 74% of all insider threat incidents according to the resent survey of Ponemon, and causes an average cost of $484,931 per incident.
Examples would be cases of the insiders sending confidential e-mails to wrong addresses due to human error, or using applications that can leak data, or technical misconfigurations, or transmitting viruses by connecting personal devices to the company’s network.
But insiders can become victims themselves due to a phishing, social engineering, brute forcing, credential stuffing, and other attack vectors attacks. In these cases, the insiders act as a door to companies’ critical information and infrastructure.
- When insiders act as attackers, we talk about malicious insiders. According to Ponemon this category makes 26% of insider threat incidents at an average cost per incident of $648,062.
The reason might be that the employee is upset because of a refused salary increase, or he/she is blackmailed or simply has an opportunity to sell the internal corporate information to third parties. The motivation can be either a personal gain or the possibility to use stolen information for own business advantage.
Attack vectors are for example the sabotage of operations, stealing or leaking data, or providing external attackers with access to the company’s resources.
The risk of insider threat incidents
Cyber attacks can get costly if not resolved quickly. The latter includes direct costs as well as indirect costs, such as detection and recovery costs.
The challenge here is that hostile insiders possess a significant amount of knowledge that allows them to place effective attacks against assets of their organization. The attackers know where the critical information is located, where the “crown jewels” are hidden.
In addition, using the inside knowledge, the time to detect the attack, is in average longer than by other types of cyber-attacks.
According to IBM’s 2022 Security Report [3], it took organizations an average of 277 days (about nine months) to detect and report a data breach. The most common cause of data breaches in 2022 was stolen or compromised identity, with this type of attack taking approximately 243 days to detect and 84 days to contain.
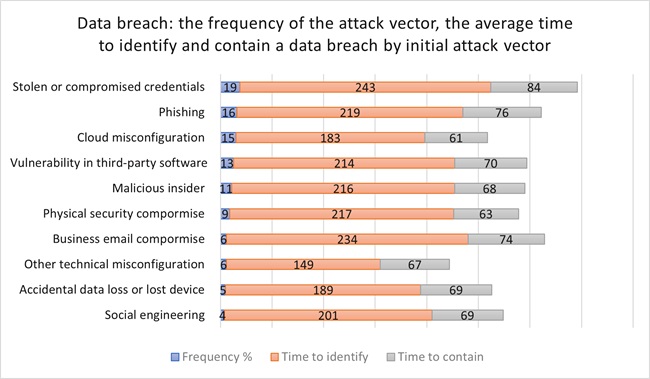
Based on the IBM Security Report “Cost of a Data Breach Report 2022”
The above graphic demonstrates that in most of the cases insiders are involved: either as attackers or they are exploited for the purposes of the external attackers.
The costs of insider threat
Insider threats are becoming more frequent, and the costs are rising.
The costs are morefold. They comprise:
- Direct costs such as money needed to detect, mitigate, investigate, and remediate the data breach.
- Indirect costs such as the value of resources and time spent dealing with the incident.
- Lost opportunity costs like losses in potential profits because of the attack.
The more time an organization needs to detect and contain the attack, the higher is the cost for the incident.
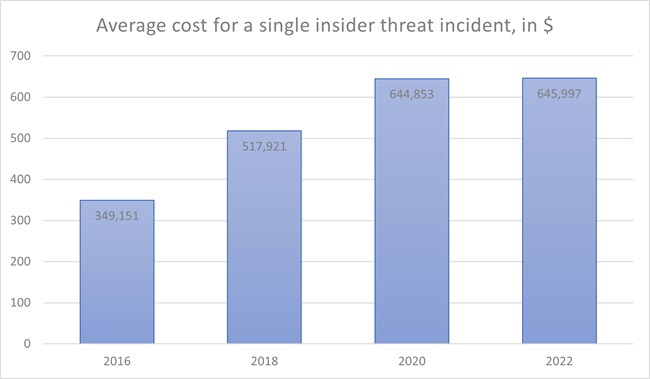
Ponemon Institute has conducted several studies on the cost of insider threats over many years. According to these studies, in average the costs for a single insider threat incident have risen by 85% between 2016 and 2022.
Source: Ponemon Institute, 2022 Cost of Insider Threats Global Report
Our solution
The core question is how to secure the information flow, the trustworthy communication with partners and how to secure know-how within the company. The weak spot is a human being; technology is nothing but a tool for information misuse. In other words, securing know-how within the company is crucial.
Cyber attacks can get costly if not resolved quickly. It makes sense to invest in preventive, security intelligence activities – it will save time and money. Furthermore, it is crucial to realize the danger before one is attacked. Information security should be part of daily business. The employees as well as the managers should be trained and well aware of risks and dangers.
Therefore, to tackle this threat, organizations should implement an information security management system throughout the company to secure and protect the sensitive information. Organizations also need a business continuity management program for being able to keep functioning during and after an emergency or major disruptive event.
And most of all, the organizations need to implement a comprehensive cybersecurity training program for all employees and contractors. The goal is to minimize the risk of insider threat incidence caused by ignorant or careless user actions due to missing knowledge on information and cybersecurity.
In all these matters Eviden and its entities like SEC Consult support you with expert knowledge.
References:
[1] Ponemon Institute, 2022 Cost of Insider Threats Global Report, https://static.poder360.com.br/2022/01/pfpt-us-tr-the-cost-of-insider-threats-ponemon-report.pdf
[2] D. Georgiev, April 2023, 22 Insider Threat Statistics to Look Out For in 2023, Techjury, https://techjury.net/blog/insider-threat-statistics/#gref
[3] IBM Security, Cost of Data Breach Report 2022