Introduction
The cloud promises agility and scalability, but how can your organization embrace it without compromising control?
Businesses are increasingly concerned with protecting their strategic digital assets, such as intellectual property and customer data, while remaining compliant. They need to maintain control over data flow and location.
With Eviden, navigating digital sovereignty considerations for business processes and cloud adoption is simpler than ever:
- Understand the sovereignty implications on your business processes
- Prioritize your sovereignty efforts and determine where to start
- Migrate complex business processes to the cloud while maintaining compliance.

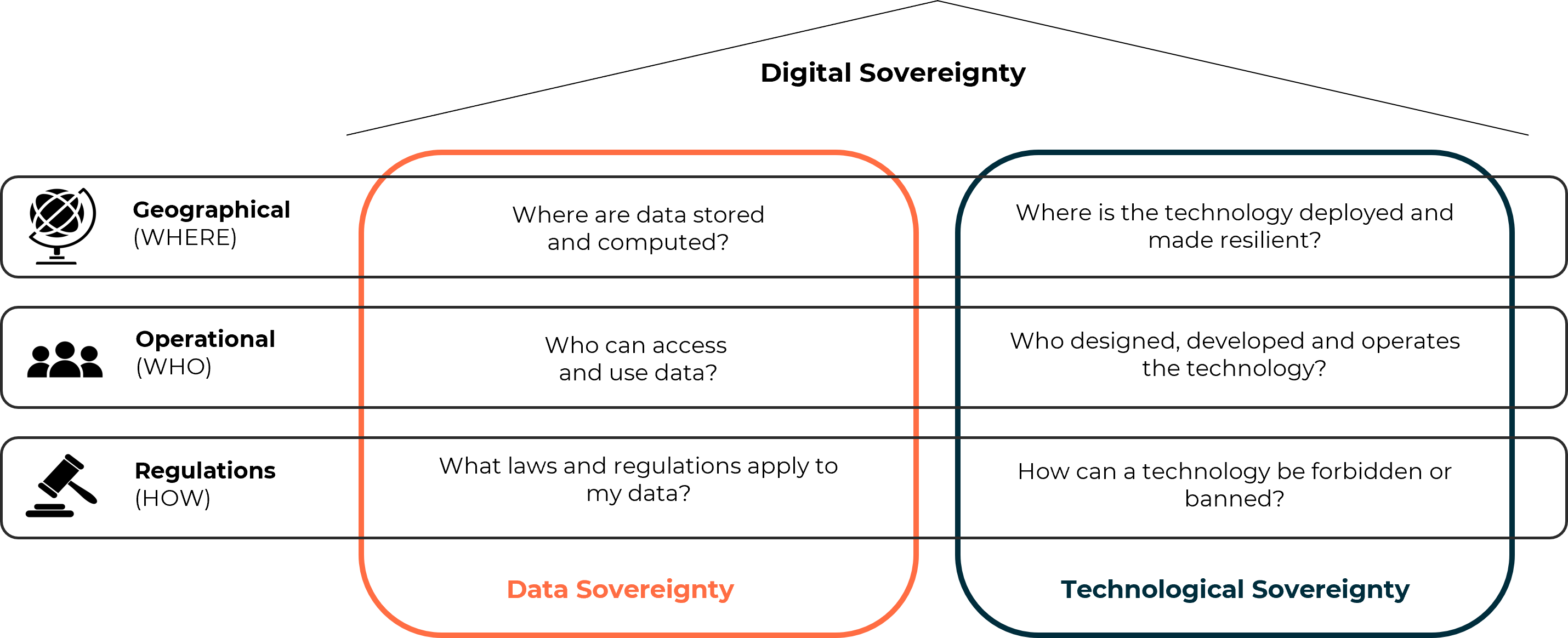
What is digital sovereignty?
Data sovereignty and technological sovereignty are the two pillars of digital sovereignty, which can be defined as the degree of control an organization has over its digital environment (data, applications, software, systems and hardware).
The complexity of digital sovereignty increases depending on the organization’s geographical, operational, and regulatory context.
Your journey to digital sovereignty with Eviden
At Eviden, we guide your journey to a secure and compliant digital future. We help you find the right balance between:
Associated with your current business and technological setup
Required to mitigate partially or totally the risks
Needed to drive business growth
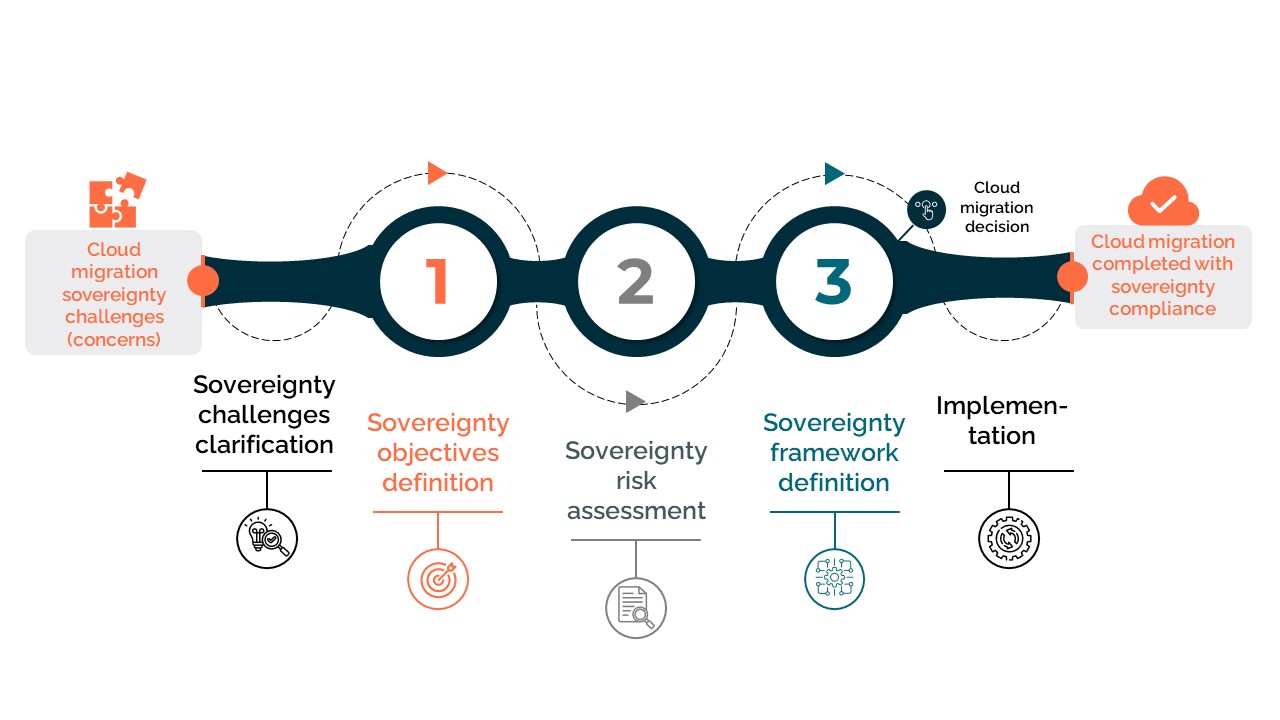
How it works
Eviden offers a unique and field-proven end-to-end digital sovereignty offering, helping you assess your specific requirements and build a secure, compliant foundation for your critical digital assets.
Eviden’s sovereignty risk-based assessment methodology helps you identify the relevant cloud architecture for each of your application sovereignty needs.
We also recommend the appropriate operating model and processes for customers to govern, secure and remain compliant for your sensitive workloads. Eviden will help define a sovereignty framework according to each of your requirements.
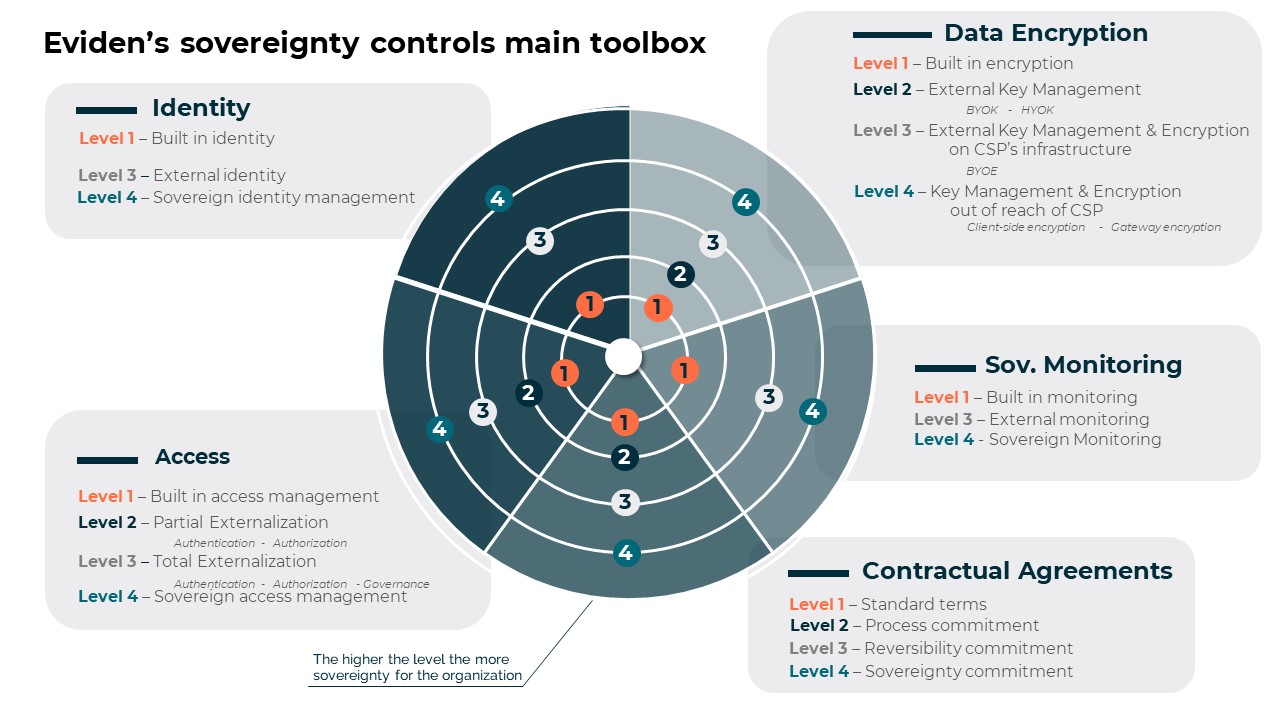
Our extensive experience in sovereign controls translates into a robust toolbox encompassing five key categories: identity management, access controls, data encryption, sovereignty monitoring and contractual agreements.
Each category offers various control levels, allowing us to advise you on the right solution to your specific use case. Furthermore, Eviden automates the enforcement of these security controls, configuration settings, and architectural requirements as defined within your unique sovereignty framework.
Eviden has developed its own comprehensive suite of sovereign security solutions developed entirely within the European Union.
Identity and access management (IAM)
Evidian, our 100% EU-designed and developed IAM solution, empowers businesses with a scalable and secure approach to identity-driven security.
It encompasses functionalities like single sign-on, federation, access governance, and identity lifecycle management.
Data encryption and key Management
For more control over encryption keys used within cloud environments, we offer Trustway Proteccio®, our Common Criteria EAL4+ certified HSM, the only ANSSI-qualified option on the market, and which is approved for use in EU restricted agreements.
Trusted digital identities
Our Cryptovision and IDnomic products enable the creation and protection of digital identities for public authorities and enterprises, as well as a complete certificate lifecycle management.
These solutions are made in Europe and can be deployed on-premise or as a service.
Why Eviden
Eviden provides a comprehensive framework of solutions designed to address the specific data sovereignty requirements of its customers across various cloud platforms, including AWS, Azure, Google Cloud, Salesforce and Webex. Through close collaboration with these partners, Eviden aims to ensure the perfect balance between agility and control for your specific cloud environment.
Navigating the complexities of digital sovereignty requires a powerful combination of:
Global and local consulting expertise
- Global network: Experienced consultants for an industrialized approach with consistent transnational standards and compliance frameworks.
- Local expertise: Deep local knowledge helping to adapt to specific laws and constraints in each region.
Actionable insights approach
- Beyond governance, risk and compliance (GRC): Translating GRC requirements into clear, actionable roadmaps that guide your implementation process.
- Technical expertise: Consulting services around cryptography, IAM and other critical areas to turn strategy into actionable plans.
Global delivery with optimized costs
- Easy implementation: Global approach leveraging proven methodologies for consistent, high-quality delivery across all projects, customized to your needs.
- Cost optimization: through Managed Security Services (MSS) and compliant operations.
Legitimacy in cryptography
- Certified products: NATO-certified R&D products for PKI and HSM.
- Expert team: Experienced consultants, integrators, and crypto experts & Scientific Community.
- Successful customer deployments: Proven track record of delivering secure digital sovereignty solutions.
Related resources
Navigate your digital sovereignty journey with our experts through every step, from identifying your unique sovereignty challenges and goals to implementation while ensuring full compliance with sovereignty requirements.
Get in Touch!