What is a gateway?
According to ANSSI, to exchange data between two information systems (IS), it is necessary to establish an interconnection between them. An interconnection is a device or a set of devices that enables the transfer of information between two information systems.
Eviden gateways enable cybersecurity-protected interconnection between critical systems with different confidentiality levels and/or different domains.
In other words, they enable unidirectional or bidirectional data transfer between systems with different confidentiality levels (e.g., open <> confidential, secret <> top secret) and/or different domains (e.g., air, land, sea).
It is this dual, multi-level/multi-domain approach that enables us to meet the needs of collaborative combat.
Why deploy MLS gateways within critical system chains?
- Enable the exchange of critical data through a network-centric architecture: use MLS gateways for cyber secure connectivity of data.
- Control the sharing of critical information by compartmentalizing your system chains, thereby ensuring the sovereignty and integrity of your missions and the data exchanged.
- Anticipate threats and security requirements to maintain the operational availability of platforms.
What we bring to the table
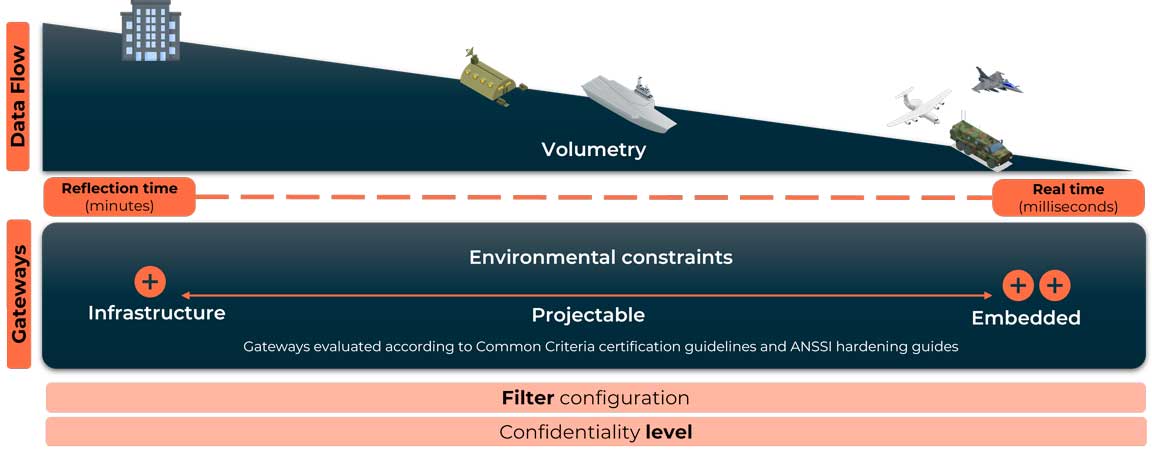
From infrastructure to embedded systems, we provide a comprehensive range of capabilities to meet your operational and functional needs. We support you from the definition of your use case, the definition of architecture, the qualification & certification, to the industrialization and integration.
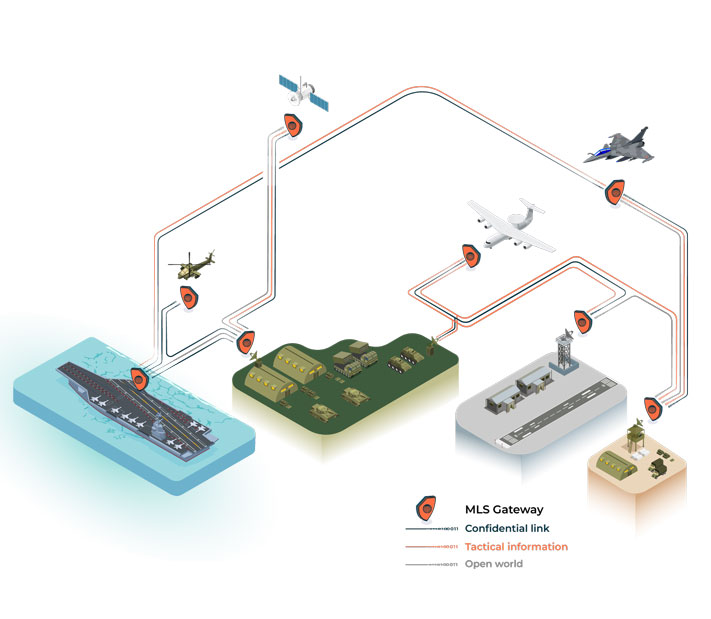
Operational challenges

Sovereignty
Control the exchange of critical information by compartmentalizing system chains, thereby ensuring the sovereignty and integrity of missions and data exchanged.

Connectivity
Guarantee the secure exchange of "authorized" information between different worlds, with different levels of confidentiality.

Flexibility
Integrate increased computing power to boost the operational capabilities of carriers in service via a scalable computer.

Interoperability
Enable secure exchanges through C2s in the context of a joint H<>J operation.

Integrity
Control and guarantee the integrity of sensor data to be transmitted to a secure remote IT infrastructure.
We provide solutions tailored to every operational need: from reflection time to real time, from infrastructure to embedded system.
Key capabilities of our MLS Gateway range
- Domain segregation (multi-domain, multi-level)
- Real time, near real time, reflected
- Content control (content disarm reconstruction)
- Data filtering
- (cross domain guard)
- Flow and identity control and management ("whitelist")
- Protocol breaker
- Flexible and scalable architecture
- Modular architecture (mono, bidirectional) for business intelligence
- Content Disarm and Reconstruction CDR
- Deep Content Inspection
- Integration of our own applications
- Software and hardware hardening
- Resilience, autonomy, degraded mode
- Secure boot, chain of trust
- Zero-trust; security by design; data-centric approach
- Security hypervisor (CC-evaluated)
- Strong administrator and user authentication
- Operational supervision/SIOC
- Cryptographic resources
- High availability; Business continuity plan (BCP): operational availability, relay (high availability)
- Sanitization
- Compliant with the CC EAL4+ evaluation director schema – preparation to be evaluate with National French agency
- Constrained environment (environmental standards (DO 160; MIL-STD 810))
- Modular form factor [2MCU; 12U]
- DO254 – (DAL D to A)
- DO178
- NATO/EU interoperability (STANAG, etc.)
- Video streaming STANAG 3350; ARINC 818
- Compliance with ANSSI PA101 guide
Our clients
FAQ
According to ANSSI definitions,
- Multi-level interconnection: interconnection between a classified information system and an unclassified information system or a system with a different classification level.
- Multi-domain interconnection: interconnection between information systems with the same classification level or equivalent classifications (Secret <> NATO Secret).
Logic |
Data-Centric Security |
Zero Trust |
|
Key point |
Data |
Access |
|
Key question |
Who can use this data and how? |
Who is attempting to access it and can they be trusted? |
|
Approach |
Intrinsic protection of information |
Constant identity and context control |
|
What does this mean for secure gateways? |
The gateway protects the data itself (classification, encryption, distribution control), regardless of the network. |
The gateway does not trust any traffic by default and systematically verifies identity and context. |
Our solutions cover 90% of ANSSI requirements. The remaining 10% relate to the customer’s organizational requirements.
It is supported by the industrial expertise and facilities of our Aix-en-Provence defense site.
Contact us