Our Approach

Compliance and Sovereignty with Cloud Scrutinize
Cloud Scrutinize is your trusted partner for ensuring cloud compliance within the public sector. We offer expert guidance on enhancing security and minimizing risks in accordance with national regulations, data protection laws, and best practices. Our solutions ensure a secure and resilient infrastructure for your administration.

Digital Sovereignty
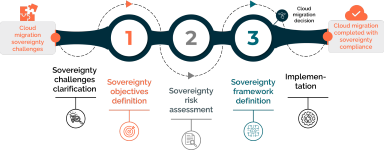
Eviden offers a unique and field-proven end-to-end digital sovereignty offering, helping you assess your specific requirements and build a secure, compliant foundation for your critical digital assets. Through strategic initiatives and robust frameworks, we ensure data privacy for citizens, fortify critical infrastructure, and foster independence from foreign dependencies.

Cloud SecOps Center
The Eviden Cloud Security Operations Center, located in the European Union (Romania/Timisoara), boasts a skilled team proficient in Cloud and DevSecOps. It proactively prevents cloud misconfigurations, safeguards data from threats, and maintains security posture, minimizing complexity, risk, and costs associated with cloud security.
Want to learn more?
Connect with us to discuss your transformation needs and challenges and get support from our experts