As every chief information security officer (CISO) knows, the major risk in IT is between the chair and the laptop. It is even worse in the mobile landscape as the users are outside alone and connected to multiple public networks such as their mobile operators, WiFi networks and foreign networks. In addition, shadow IT, i.e., the use of applications not validated by the IT department, is widely used by every user in the mobile world. Just look at your own smartphone and all the applications you have downloaded. Honestly, who remembers the rights which have been given to those apps? If you add the bring your own device (BYOD) policy, you are now at risk of being attacked.
Mobile network operators’ role in infrastructure security
On the infrastructure side, the mobile network operators (MNOs) are doing quite an effective job to protect their infrastructure. But their main objective is to make sure their networks work properly, not necessarily that your data is safe.
Indeed, it is a bit like managing a road or a highway.
The operator ensures the infrastructure is in good condition for driving but cannot be responsible for the car’s quality or the driver’s physical conditions. In fact, the highway company has nothing to do with drivers who are drunk, under narcotics, sleeping, or sending an SMS while driving. In such a situation, everything can happen, from cheap malware embedded in game apps to spoofing. Besides this first issue, there are some more that are directly linked to mobile networks and mobile phones:
The SIM card: Although it is a secure element provided by your network provider, which is secured by principle, things can be done remotely especially while roaming.
The signalization protocols such as Diameter and SS7: These are key vector attacks by fake mobile virtual network operators (MVNOs) who benefit from access to all operators thanks to international roaming protocols. The first thing they can do is ask where you are.
The mobile phone: This is a radio Christmas tree with plenty of ports that can be attacked such as WiFi, Bluetooth or NFC, just to name a few. Put your smartphone in tethering mode next time you take the metro. Transform your smartphone into a WiFi hotspot and you will see dozens of terminals. It is then rather straightforward to provide them with WiFi access and to do a man-in-the-middle attack.
Public charging points: Airports and other public facilities often have USB ports to recharge your smartphone. It is a bit like drinking water from a river in a large city. You simply don’t know what you are drinking.
The operating system and the underlying chipsets: It is great to have automatic upgrades but who does them and why should you trust the servers doing that remotely without some security clearance?
Solutions for secure smartphones
Solutions exist. And, as always, the more secure you want to be, the more constraints you will face. It is up to you to put the target. In the table below, we have put four levels in front of the major threats:
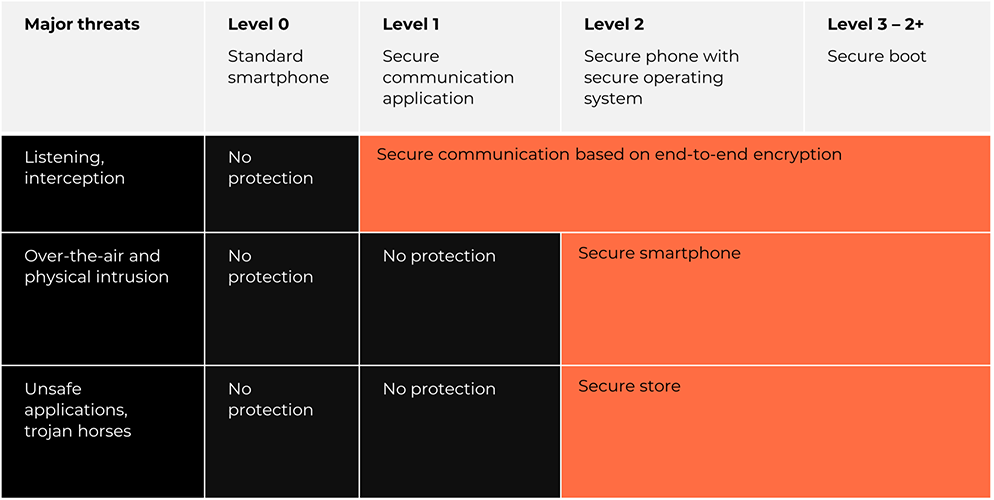
The critical role of secure smartphones in government communications and military operations
Knowing that more and more governments will shift their narrowband radio systems such as Tetra and Tetrapol to 4G/5G networks with some network sharing with mobile operators, it is even more important to rely on secure smartphones. Imagine if the entire homeland security forces of a given country are without any connectivity because of a virus or malware. No more police, firemen, or ambulances. On the military side, it is even more important as such devices can be part of blue force tracking and battle management systems.
Eviden believes in a secure and sustainable future and has a spectrum of offerings around smartphone security such as secure OS, secure boot, secure communication, secure mobile certificates, secure central system, secure app store and hardware security modules. Some of these technologies are already deployed by homeland security forces and soldiers in their daily operations, reiterating Eviden’s commitment to participate in a safe digital environment.
Learn more about our critical communications solutions.


