Among the various requirements outlined by the Digital Operational Resilience Act (DORA), one of them stands out: the mandate to have frequent security tests. It isn’t a simple recommendation anymore, but a regulatory obligation for financial institutions to ensure they won’t only be resilient, but also proactive in identifying and mitigating potential vulnerabilities before they can be exploited.
In this blog post, our attention is directed towards the necessity outlined in the DORA to incorporate Threat Led Penetration Testing (TLPT) within the information and communications (ICT) risk management framework and the digital operational resilience strategy.
A deep dive into DORA’s testing requirements
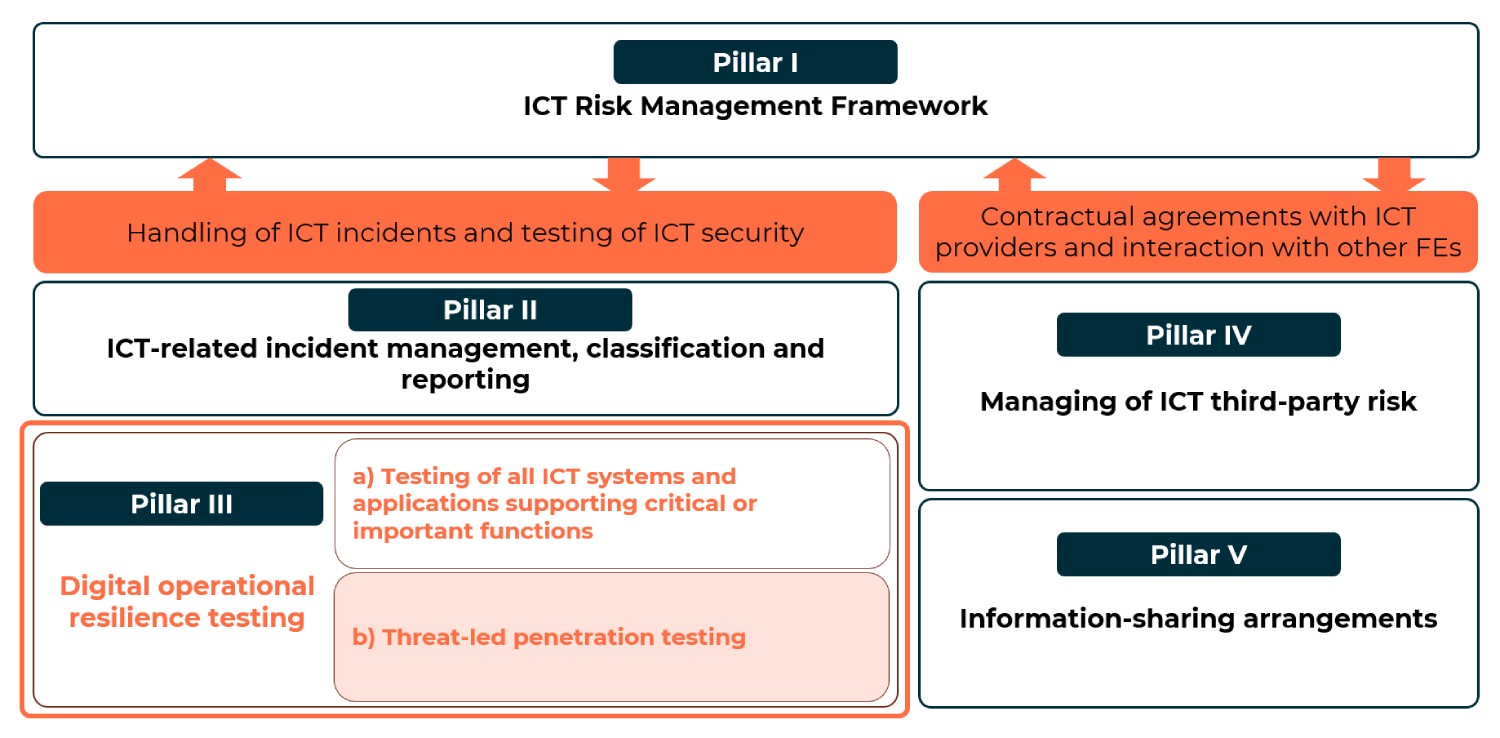
As part of the digital operational resilience testing framework, DORA outlines two primary forms of security testing:
- Security testing of all ICT systems and applications that support critical or important functions. You can read more about the key aspects of this first component.
- Advanced testing of ICT tools, systems and processes based on threat-led penetration testing (TLPT).
In the subsequent analysis, let us examine the key aspects of the second component — threat led penetration testing.
Covering the legal bases
The core requirements for TLPT are laid down in Articles 26 and 27 of DORA.
The more detailed provisions are maintained in a separate Regulatory Technical Standard (RTS). The European Supervisory Authorities (ESA)’s final report on the draft RTS was published on July 17, 2024: Final report on Regulatory Technical Standards specifying elements related to TLPT. In the next step, the RTS will be adopted by the European Commission, reviewed by the European Parliament and the Council. This will be finally published in the Official Journal of the EU.
TLPT: The latest security framework
The threat led penetration test (TLPT) is a new security method introduced with DORA. At its core, it is based on the TIBER-EU framework but includes advanced requirements, such as the mandatory purple team testing. Therefore, it is important that TIBER-EU and TLPT should not be considered the same method with just another name.
According to DORA Article 3 (17), the “threat-led penetration testing (TLPT) means a framework that mimics the tactics, techniques and procedures of real-life threat actors perceived as posing a genuine cyber threat, that delivers a controlled, bespoke, intelligence-led (red team) test of the financial entity’s critical live production systems”.
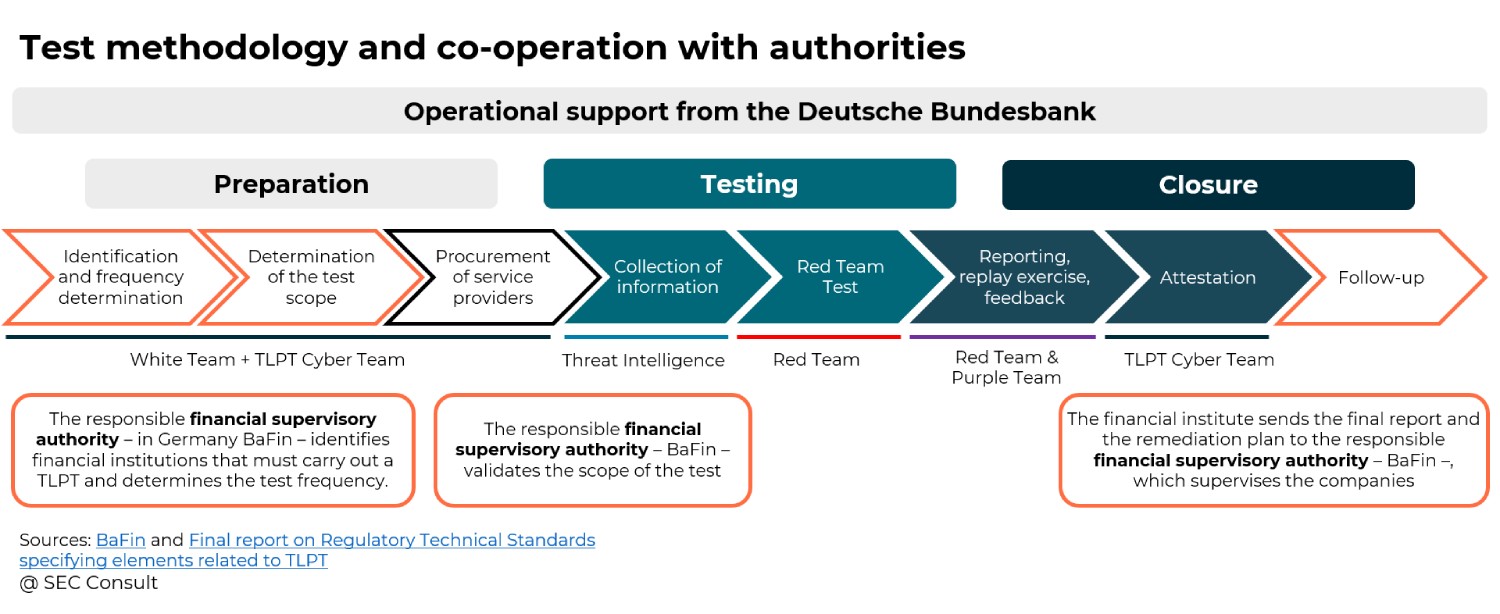
However, TLPT will only be applicable for select financial institutes. Those who need to perform the test will be informed by their respective competent authorities.
If tasked, the financial institute must conduct the TLPT focused on their critical functions and services. These tests must be routinely carried out at least every three years. They will be executed on live systems, with the precise scope determined by the financial organizations and validated by the relevant authorities.
To prepare for these tests, financial organizations must identify all relevant ICT processes, systems, and technologies that support their critical functions and services, including those managed by third-party ICT service providers. If third-party providers are involved, the financial institution must ensure their participation in the testing process.
Upon completing the threat led penetration testing, both the financial institution and the external testers must submit the necessary documentation to competent authorities, confirming that the tests were conducted according to the required standards. The competent authorities then review the documentation and issue a certification.
A roadmap for a seamless TLPT journey
The TLPT is intended to enable financial institutions to realistically assess their ability to defend against and respond to cyberattacks, thereby ensuring the resilience and security of critical financial systems.
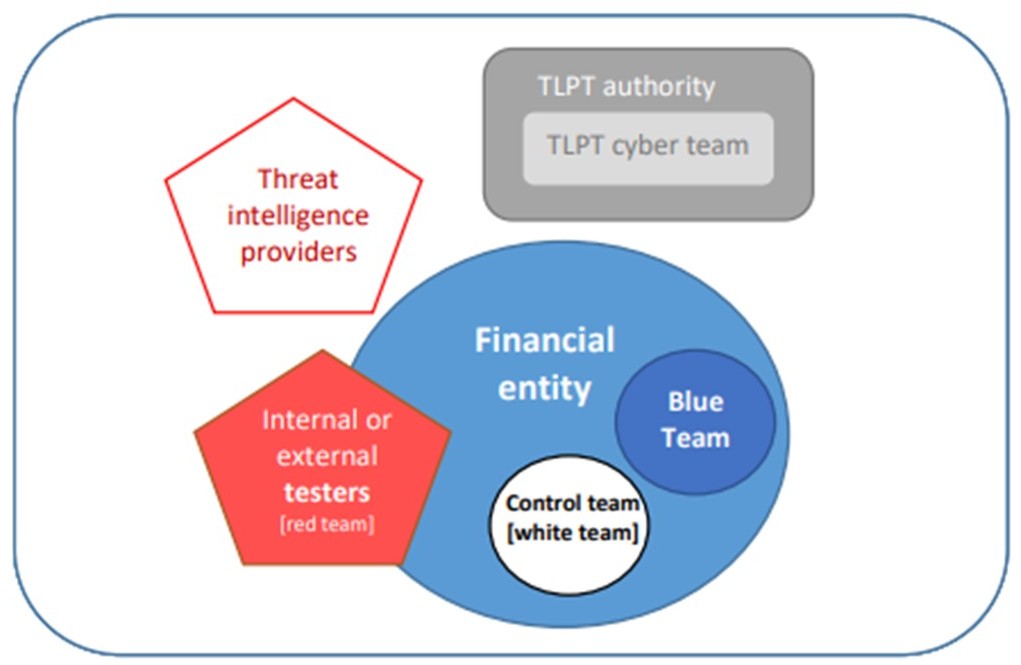
The main participants of the TLPT and their tasks are indicated in Fig. 2:
- The TLPT Cyber Team (TCT) consists of personnel within the TLPT authority responsible for overseeing all operational aspects of TLPT-related activities. This team may include roles such as test managers.
- The Threat Intelligence Provider replicates a hacker’s information-gathering activities by leveraging multiple reliable sources.
- The Control Team, also known as the White Team, manages the TLPT from the perspective of the financial entity undergoing the exercise. Their responsibilities range from procuring external providers and conducting risk assessments to overseeing the daily testing operations and managing risks. The Control Team leader must have the necessary authority within the financial entity to oversee all aspects of the test without compromising its confidentiality.
- The Blue Team consists of employees tasked with defending the financial entity against simulated or actual cyber threats, unaware that they are being tested.
- During the active red team testing phase, the Testers, or Red Team, employ a range of tactics, techniques, and procedures (TTPs) to rigorously test the financial entity’s live production systems. These TTPs typically include the following activities:
- Reconnaissance – Gathering extensive information on the target
- Weaponization – Analyzing infrastructure, facilities, and employees to prepare target-specific operations
- Delivery – Launching the full operation on the target
- Exploitation – Compromising the financial entity’s servers, networks, and staff through social engineering
- Control and movement – Attempting to pivot from compromised systems to other vulnerable or high-value targets
- Actions on target : Compromising systems even further to gain access to predefined target information and data as outlined in the red team test plan
As far as the TCT is concerned, the DORA leaves it up to the Member States to designate the responsible authorities and their tasks. Therefore, the implementation of the TLPT may vary from one Member State to another. In Germany, for example, the tasks have been divided between the national central bank Deutsche Bundesbank and the Federal Financial Supervisory Authority, BaFin. BaFin is the competent supervisory authority and is responsible for supervisory tasks in connection with the TLPT while Deutsche Bundesbank is responsible for the operational support for the TLPT.
Consult. Support. Comply.
Since the introduction of the TIBER framework, SEC Consult has supported several customers in carrying out these tests.
Based on our experience and knowledge, we are confident of supporting our customers by creating a suitable test plan and performing the threat-orientated penetration tests according to DORA. This not only ensures compliance with DORA requirements, but also strengthens your ICT network against cyber threats.
Find out more about threat led penetration tests for your DORA compliance journey.