Innovation from the fourth industrial revolution is providing industrial organizations with opportunities for significant change, delivering huge benefits to drive digital transformation and reduce risk. But, as with every emerging innovation, the benefits come with associated uncertainties that must be managed to ensure those benefits are achieved safely and securely. As industrial companies work to extend their competitive advantages and modernize, they are converging operational technology (OT) and information technology (IT) infrastructure. In many cases, legacy OT is interconnected and enhanced with digital capabilities.
In this article, we explore some of the key trends in OT security in 2024 and provide some expert insights and trends in the OT security arena.
If you connect, you must protect
In the new world of increased IT/OT convergence, air gapping provides a false sense of security and amplifies the attack surface. Adversaries understand OT systems are mission-critical and, in many cases, even affect the health and safety of societies. OT security incidents have seen an increase in the recent years. The cost of OT Security breaches can be substantial and, in some cases rise to over $100 million. This trend will lead to significant downtown, loss of production and data, but most importantly it can have grave consequences if it has the potential to compromise physical safety of employees, especially those working in industrial environments such as plants, factory floors and engineering facilities. Therefore, OT security and safety is critical to support vital everyday operations.
The 5 key OT security trends for 2024
As OT security takes front and centre stage in 2024, here are the top 5 key trends we will observe:
Trend 1: OT environments will continue to be the target of more direct and indirect attacks.
Trend 2: Expanding regulations, especially NIS2, will be a pivotal driver for OT security in 2024.
Trend 3: There will be a shortage of well qualified and experienced OT security specialists.
Trend 4: There will be increased focus on OT security training and awareness.
Trend 5: There will be a relentless focus on collaboration and knowledge sharing across IT, OT and security teams.
Importance of effective OT security governance
It is no secret that OT and IT are becoming increasingly connected, but this can also blur governance and reporting lines. We advise companies to take the time to define OT organizational structure, reporting lines, roles and responsibilities. Some of the key questions around a business’ OT security governance should include:
– Where does OT security authority and accountability reside?
– Who decides if a specific device needs to be patched? (Note that OT security devices cannot be patched in the same way as most IT devices.)
– How will you help drive collaboration and establish common ground with the CISO, IT SecOps and OT teams?
People and culture play a big role
Peter Drucker, one of the most widely known and influential thinkers on management came up with the phrase “Culture eats strategy for breakfast.”
The same holds true for OT security. A secure, safe and trusted OT environment must be underpinned by building a strong awareness culture where people play a major role to enable cyber resilience. Security training and awareness for plant managers and engineers is absolutely imperative to help drive change and foster a strong security culture.
Introducing an inside-out approach to OT security
There is no silver bullet to address OT security. Industrial organizations are faced with a growing number of challenges that cannot be solved solely by technological solutions. The journey to a secure and trusted OT environment requires a multi-faceted, inside-out framework to protect the entire industrial attack surface, starting with the devices, as shown in the figure below.
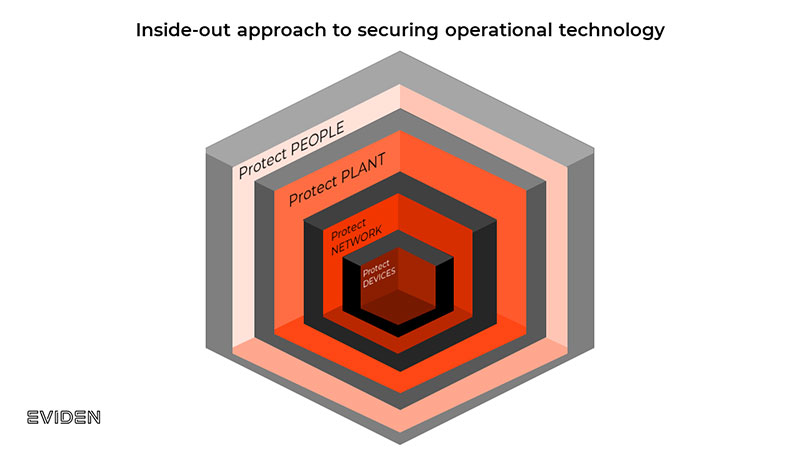
There is a wise saying in security that you can’t protect what you can’t see. And for that reason, asset visibility forms the foundations of an inside-out approach that drives an OT-resilient architecture.
There are many benefits of using an inside-out approach for OT security. Some of these are as follows:
- Encourages a systemic and comprehensive approach to developing a safe and secure OT control environment;
- Provides the building blocks for an OT security strategy and improvement program;
- Provides a foundation to foster collaboration and knowledge sharing across the enterprise;
- Provides consistency in interpreting OT security needs, and is universally applicable within any OT or ICS environment;
- Provides a common language to drive OT security decisions and investment.
For the safety capabilities of networked plants and machines to grow with the risks, a uniform understanding of an overarching OT strategy is first needed. This is because corresponding plants and systems are often distributed across different business units without a strategic orientation, or any regard to technological leaps or service provider integration. Therefore, there is often no corresponding role to discuss, coordinate and take responsibility for such considerations and developments across the board.
An OT coordinator or an OT architect is needed here. The overarching industrial security strategy must then be aligned with this OT strategy. The integrated consideration of OT security, IT security, physical security, business continuity and integrated product security from the initial concept to quality-of-life maintenance long after delivery is elementary.
Keeping up with the evolving nature of cyberattacks
Attacks on OT/ICS infrastructure will continue to increase in number, in impact and in sophistication. This is because many organized groups see specific goals, including business goals:
– Fast money with ransomware
– Geopolitical reasons like hybrid war, market manipulation, and competitiveness
– Disrupted operation of the critical infrastructure
– Slowing down the competition
– Rich variety of IPs
– Weakened infrastructure
– Hacktivism
– Insiders mistakes
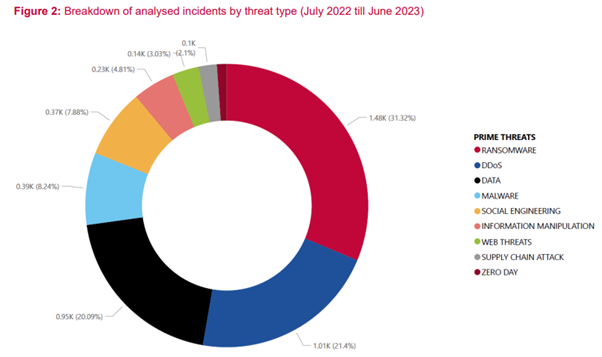
The more important the targets, the better the prospect of earning, and so the more time they will devote to preparing an attack. As of today, there are nearly 30 organized international groups that have developed techniques, tactics, and procedures for attacking organizations’ ICS/OT teams. As we see from the ENISA Threat Landscape Report, that considers mainly targeted attacks, adversaries spend most of their efforts on ransomware attacks. The most impacted was the manufacturing industry with nearly 14% out of all ransomware events. Undeniably, ransomware will have the biggest impact on all industries. Nevertheless, other important types of the attacks, that might affect energy and utilities, manufacturing, and transportation, are equally dangerous.
It is loss of data, including IP and PII, information manipulation and supply chain attacks.
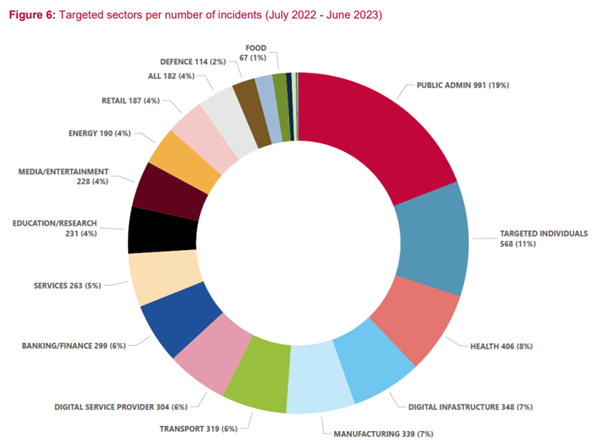
Focusing on industrial (OT/ICS) sectors, we can see that general manufacturing (this includes discreet manufacturing, chemicals, textile, machinery, automotive, electronics and more) is one of the most targeted business groups.
Threat predictions for 2024
We can be sure that 2024 will bring us more attacks. Further, we predict:
- Continuous increase in ransomware attacks
- Further adoption of AI-powered attacks in the areas of:
- Spam and phishing campaigns generation
- Malware creation, that will be hard to detect
- Vulnerabilities discovery and exploitation, including zero-days
- External data harvesting for better attack preparation
- IoT vulnerabilities and its inadequate protection
- Rise in IT and OT attacks for ICS and OT
- Vehicle hack
- Supply chain attacks
- More precise attacks on Edge devices
Undeniably, ransomware will have the biggest impact on all industries, ranging from public sector and Defense, to healthcare, general business (up to critical Infrastructure) and all kinds of manufacturers. However, 2024 top trend predictions do not detract from the importance of other attacks that might affect energy and utilities, manufacturing, and transportation, which are equally dangerous, such as loss of data, including IP and Personal Identifiable information (PII), and information manipulation.
Most common threat vectors
Constant development of new technologies, such as Artificial Intelligence (AI), will make attack easier to be performed. Despite new technologies adoption, cybersecurity defenders will fight with well-known threats, such as:
- Social engineering with a strong focus on phishing and spear-phishing
- USBs as this old threat is still alive within the ICS/OT landscape
- Known exploited vulnerabilities (KEV) as an entry point, lateral movement and foot-hold point
- Supply chain attacks
- Distributed denial-of-service (DDoS)
- Software development flaws
- Stolen credentials
- Business e-mail and/or application compromises
Remember, an IT attack is dangerous, but an OT attack is riskier and much more dangerous. This is due to the different nature of the attack and its consequences. Often IT security specialists, who have not been properly trained in handling an OT incident, will have more difficulty in efficiently and appropriately managing a risky situation.
How to limit potential impact?
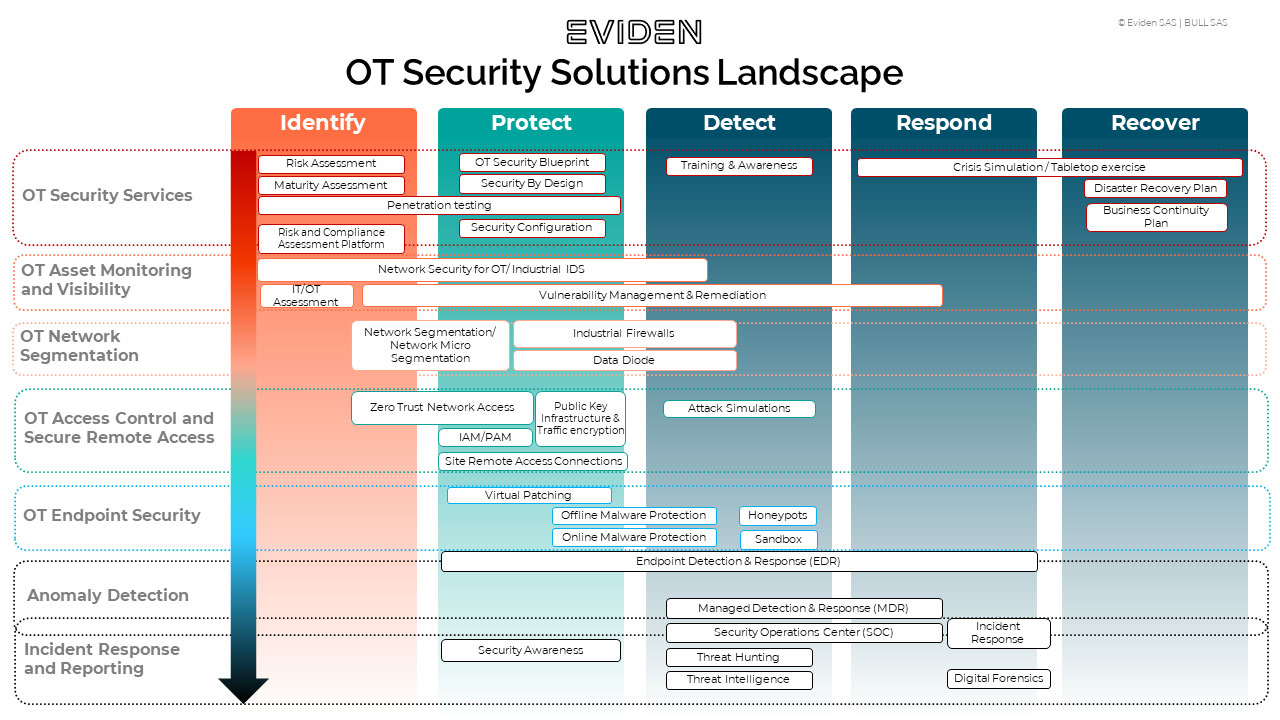
Protecting OT systems from cyber threats is paramount to maintaining the reliability, safety, and integrity of critical industrial processes. And for this reason, we advocate a holistic and integrated approach to OT security, starting with a comprehensive IT/OT risk assessment all the way through to Managed Security Services, as shown in the figure below.
Our approach is collaborative, pragmatic and business-led, and utilizes a fully integrated methodology from consulting to technology delivery.
Organizations that operate on IT and OT infrastructures should be prepared to defend against attacks in the long term. This is possible with an appropriate OT security strategy. Depending on an organization’s scale and risk profile, its Board of Directors or CISO could include end-2-end security monitoring and resilience in its strategy. This also includes the company’s supply chain. The most important aspect is to answer the critical question — “where should we start?”
Good practice says that it is good to start with a company risk profile that will include threats from organized groups (APT) and individuals (insiders or through employees’ mistakes). Subsequently after assessing risk profiles and risk factors, the organization can describe strategic milestones and align their target operating model.
Such a strategy should be based on good benchmarks such as IEC 62443, ISO 27001, NIST CSF and its various permutations such as NIST 800-161 or NIST 800-82. Among typical GRC requirements, these recommendations also include the following:
- Network segmentation – a technique that will help limit the impact of a possible attack
- Asset visibility and monitoring, including vulnerability management
- OT access control, including zero trust access mechanisms as well as encryption, identity and privilege management, and site remote access
- Supply chain risk management
- Endpoint security for modern and legacy workstations
- Incident detection, response and reporting
- Backup and disaster recovery strategy
For a better understanding, take a close look at the illustration of the technology landscape given below.
Current and future ICS/OT prevention trends
With the latest trends and our customer requests, we observe that more and more organizations are trying to adopt multi-technology strategy to protect shopfloor. In some organizations, the OT strategy includes the innovation path as well. The most popular strategies contain:
- Risk maturity and modelling
- Cybersecurity awareness training of the personnel
- Cross-technology integrations, that will help to detect and contain threats faster, like OT IDS integrated with MDR and OT NGFW
- Adoption of virtual patching for OT networks and devices
- Implementation of the 24/7 OT SOC
Another emerging trend in the ICS/OT security is as follows:
- Adoption of vulnerability management process and tools for OT ecosystem coverage
- Implementation of IAM solutions across IT and OT environments
- Dedicated site remote access technologies, integrated with IAM for better control over contractors and supply chain processes
- OT EDR and legacy endpoint protection systems installation
- PKI, a technology that is still underestimated in the OT world, but is gaining more and more popularity, especially in the transportation industry
NIS 2 gives wind to the sails
All the above-mentioned trends can be correlated with other challenges that will have significant impact on the manufacturing, energy and utilities, transportation and healthcare sectors – the NIS2 directive.
With respect to critical and essential entities, the European Union aims to enforce the mechanism of reporting breaches to country-level organizations (CERTs). The NIS2 Directive that will be adopted by all EU States by the end of October 2024 generates additional obligations for those entities, such as:
- Basic cyber security hygiene and trainings
- Assets management
- Access control
- Improved cyber security management system by mandatory policies for risk analysis and information system security
- Use of additional encryption and MFA mechanisms for text, video and voice communications, where appropriate
- Security effectiveness assessment
- Supply chain security management
- Incident prevention, detection, response and handling capabilities
- Crisis management, business continuity and disaster recovery
In summary, all aspects that mature organizations should include in their mature security strategy will be monitored and penalized by local governments.
Recognizing threats. Securing systems.
It is encouraging to see that investments in OT security are growing rapidly and while Industry 4.0 provides businesses with a plethora of opportunities, the growing convergence between IT and OT environments is not going to slow down. The fact remains that, on average, paid ransoms vary from 0.6 to $1.5 million per organization, and global ransomware damage costs predicted in 2031 will exceed $260 billion, along with increased insurance fees, and additional losses from downtime of production lines.
Threats to OT security should be seen as a real and present danger that not only compromise the security of data but can also compromise the safety of critical systems as well.
OT security should be seen as enabler that will help drive growth and competitive advantage.
Eviden’s OT security solutions are designed to help businesses navigate through the complex ecosystem and manage OT security risk more effectively by adopting an inside-out approach covering identification, detection and response. Understanding the changing landscape is the first step to brace yourselves and your businesses for any possible threat or risk. Partnering with an expert is the next. Make your OT security dream come true today—understand, identify, detect, partner and respond securely.